EDR without NDR with weaknesses in protection
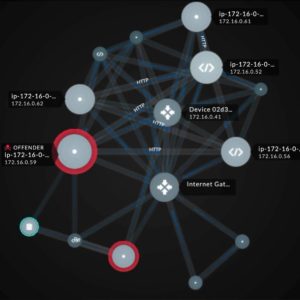
The Swiss security company Exeon Analytics warns against only relying on conventional EDR solutions (Endpoint Detection & Response) when securing endpoints. Because the agent software does not always run at the end point, which creates weaknesses in the defense network. Many endpoints in modern, hybrid networks do not support the agents required for this, and where such agents are running, they can be undermined and deactivated by sophisticated attacks. Also, because of the trend towards working from home and BYOD (Bring Your Own Device), IT and security teams often don't have access to privately owned endpoints...