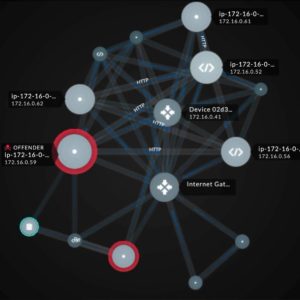
With AI-based NDR against ransomware
Ransomware threats are constantly increasing and evolving. AI-supported NDR (Network Detection and Response) systems can keep up better and therefore offer more protection. According to the Swiss security company Exeon Analytics, with the emergence of the Akira ransomware, large companies in particular and those tied to Kritis or NIS 2 are facing a new danger, as there is currently no decryptor for the current versions of the malware and the new group is mainly focuses on victims from whom it can extort large ransoms. According to Erismann, many SIEM systems (Security Information and Event Management) offer...