Thanks to Europol, there seems to be an end to the FluBot Android malware for the time being. The European Authority announces that, with the help of other national law enforcement agencies, it has disabled the network and structure of the SMS-based FluBot spyware for Android.
An international law enforcement operation involving 11 countries has resulted in the fight against one of the fastest-spreading mobile malwares to date. Known as FluBot, this Android malware aggressively spreads via SMS, stealing passwords, online banking details, and other sensitive information from infected smartphones around the world. Its infrastructure was successfully disrupted by the Dutch Police (Politie) in early May, rendering this malware strain dormant.
Europol: FluBot network under control
This technical achievement follows a complex investigation involving law enforcement agencies from Australia, Belgium, Finland, Hungary, Ireland, Spain, Sweden, Switzerland, the Netherlands and the United States, with international activities coordinated by the European Cybercrime Center ( EC3 ). The investigation is ongoing to identify the individuals behind this global malware campaign.
How FluBot worked
First discovered in December 2020, FluBot has gained prominence in 2021, compromising a large number of devices worldwide, including significant incidents in Spain and Finland.
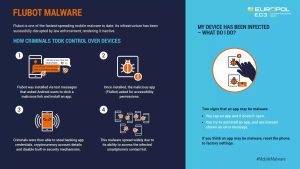
The malware was installed via text messages encouraging Android users to click a link and install an application to track a package delivery or listen to a fake voicemail message. After installation, the malicious application, which was actually FluBot, asked for access permissions. The hackers would then use this access to steal banking app credentials or cryptocurrency account credentials and disable built-in security mechanisms.
This malware strain was able to spread like wildfire due to its ability to access an infected smartphone's contacts. Messages with links to the FluBot malware were then sent to these numbers, which helped spread the malware further and further. This FluBot infrastructure is now under the control of law enforcement agencies, stopping the destructive spiral.
International police cooperation
As cases spread across Europe and Australia, international police cooperation was key to taking down FluBot's criminal infrastructure.
Europol's European Cybercrime Center brought together national investigators in affected countries to develop a common strategy, provided digital forensic support and facilitated the exchange of operational information needed to prepare the final phase of the operation. The J-CAT hosted at Europol also supported the investigations. On the day of the takedown, Europol also set up a virtual command post to ensure smooth coordination between all the authorities involved.
My device has been infected - what can I do?
FluBot malware is disguised as an application, so it can be difficult to detect. There are two ways to determine if an app might be malware:
- When you tap an app and it doesn't open
- If you try to uninstall an app, you'll get an error message instead
If you think an app might be malware, factory reset the phone.
Learn more about it how to protect yourself from mobile malware .
The following authorities were involved in the investigation:
- Australia: Australian Federal Police
- Belgium: Federal Police (Federale Politie / Police Fédérale)
- Finland: National Investigation Bureau (Poliisi)
- Hungary: National Investigation Bureau (Nemzeti Nyomozó Iroda)
- Ireland: A Garda Síochána
- Romania: Romanian Police (Poliția Română)
- Sweden: Swedish Police Authority (Polisen)
- Switzerland: Federal Office of Police (fedpol)
- Spain: National Police (Policia Nacional)
- Netherlands: National Police (Politie)
- United States: United States Secret Service