A new zero-day remote code execution bug in Microsoft Office is causing a stir. More specifically, it is likely a code execution vulnerability that can be exploited through Office files.
Based on what is known so far, there may be other ways to trigger or abuse this vulnerability. Security researcher Kevin Beaumont has named the vulnerability "Follina," which is proving to be a useful search term on the topic until an official CVE number is assigned. In addition, Microsoft has meanwhile created a an official workaround from Microsoft released. In his blog post, Sophos expert Paul Ducklin gives an insight into the background and possible solutions.
How does the Follina zero-day vulnerability work?
- Users open a DOC file containing hidden malware, which they received, for example, by e-mail.
- The document points to a normal looking https: URL which is downloaded.
- This https: URL points to an HTML file that contains JavaScript code.
- The JavaScript in turn points to a URL with the unusual identifier ms-msdt: instead of https:. On Windows, ms-msdt: is a proprietary URL type that launches the MSDT software toolkit. MSDT is the abbreviation for Microsoft Support Diagnostic Tool.
- The command line submitted to the MSDT via URL results in untrusted code being executed.
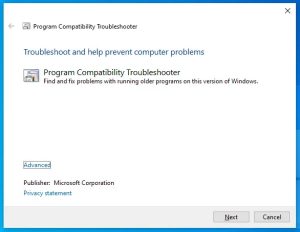
When the malicious ms-msdt: link is invoked, it triggers an MSDT command with command-line arguments like the following: msdt /id pcwdiagnostic .... When run by hand, with no other parameters, this command automatically loads MSDT and invokes the program compatibility troubleshooter, which looks harmless:
From here, users can select a troubleshooting app that will answer various support-related questions, run automated tests in the app, or report the problem to Microsoft while uploading various troubleshooting data. Although users probably do not expect to get into this diagnostic utility just by opening a Word document, the likelihood of "accepting" this series of pop-up dialog boxes is increased.
Automatic remote script execution
However, in the Follina case, it looks like the attackers came up with some unusual, but also very tricky, options to sneak into the command line. As a result, the MSDT troubleshooter does its job remotely. Instead of being asked how the user would like to proceed, the cybercriminals constructed a set of parameters that not only cause the operation to automatically continue (for example, /skip and /force options), but also a PowerShell invoke script. To make matters worse, this PowerShell script doesn't even need to reside in a file on disk - it can be provided in encrypted source code form right from the command line itself, along with any other options used. In the "Follina" case, Hammond says PowerShell is used to extract and launch a malware executable file that was provided in compressed form.
Dangerous, even with deactivated macros!
Importantly, this attack is triggered by Word referencing the deceptive ms-msdt: URL, which is referenced from a URL contained in the DOC file itself. Because of this procedure, no VBA Office macros (Visual Basic for Applications) are necessary, so this trick works even if Office macros are deactivated.
So the whole thing looks like a handy Office URL "feature" combined with a helpful MSDT diagnostics "feature". In fact, however, it creates a vulnerability that can cause a remote code execution exploit with one click. In this way, even opening a Word document prepared in this way can transmit malware without the user noticing.
In fact, Hammond writes that this trick can be turned into an even more direct attack by packaging the deceptive content in an RTF file instead of a DOC file. In this case, just previewing the document in Windows Explorer is enough to trigger the exploit without even clicking on it to open it. Just rendering the thumbnail preview window would cause Windows and Office to stumble.
What can you do?
Microsoft has already released an official workaround and will hopefully release a permanent patch soon. As handy as Microsoft's proprietary ms-xxxx URLs are, the fact that they are designed to automatically start processes when certain file types are opened or even just previewed is clearly a security risk.
Also, a commonly accepted troubleshooting technique in the community is to simply break the relationship between ms-msdt:URLs and the MSDT.EXE utility. Sophos expert Paul Ducklin provides a detailed description of this in his blog post.
Sophos products eliminate the problem
Sophos endpoint products detect and block known attacks carried out via this exploit as Troj/DocDl-AGDX. This detection name can be used to search logs for both DOC files that trigger the initial download and "second stage" HTML files that follow. Sophos email and web filtering products intercept attack files of this type, such as CXmail/OleDl-AG.
More at Sophos.com
About Sophos More than 100 million users in 150 countries trust Sophos. We offer the best protection against complex IT threats and data loss. Our comprehensive security solutions are easy to deploy, use and manage. They offer the lowest total cost of ownership in the industry. Sophos offers award-winning encryption solutions, security solutions for endpoints, networks, mobile devices, email and the web. In addition, there is support from SophosLabs, our worldwide network of our own analysis centers. The Sophos headquarters are in Boston, USA and Oxford, UK.