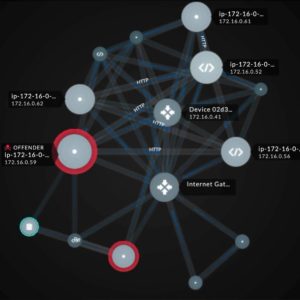
Is it an attack on IoT? – six analysis tips!
Hardware connected to the Internet of Things (IoT) can receive and forward not only data but also commands or malware code under external control. Existing sensors must not be blind spots in IT security. Six tips for detecting and analyzing attacks from the Internet of Things. IT security managers need defense methods that can detect, analyze and ward off an attack, for example via an IP camera or other sensors. Anyone who sees the resulting network traffic can block attacks at an early stage or quickly contain them in an emergency. Network Detection and Response (NDR) is a part…