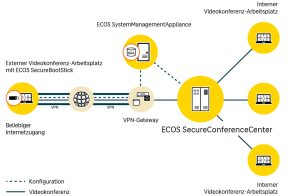
With the new ECOS SecureConferenceCenter, ECOS Technology presents a solution for highly secure video conferences. In combination with the ECOS SecureBootStick approved by the BSI for the VS-NfD level of confidentiality, a highly protected communication can be implemented.
This enables the use of video conferences even in sensitive areas. The ECOS SecureConferenceCenter can also be operated completely on-premises. This means that security-conscious companies, authorities or organizations and facilities in the critical infrastructure segment (KRITIS) retain full control over their data at all times.
Many functions for interaction and collaboration
In addition to a high level of security, the new ECOS SecureConferenceCenter also offers a high level of user-friendliness and provides all the familiar and popular video conference functions. For example, different content such as your own screen or audio and video streams can be shared. If necessary, meetings can be further divided into individual rooms via breakout rooms in order to be able to discuss particularly sensitive content in a confidential environment. Interactive collaboration between participants is possible with a multi-user whiteboard. Video conferences can also be recorded using session recording. Other functions include surveys, the use of emojis, shared notes or a chat that can be used both publicly and privately.
Simple administration via Smart Management
The ECOS SystemManagementAppliance also allows easy operation of the ECOS SecureConferenceCenter. It combines the management of the ECOS SecureConferenceCenter and the SecureBootSticks used in a single interface. In addition, seamless integration into an existing IT landscape, for example by coupling to a Microsoft Active Directory, can be ensured.
Secure access - from anywhere
If the ECOS SecureConferenceCenter is accessed from secure networks, the conference room can simply be entered via any standard browser. If employees connect externally or from other insecure networks, for example from the home office or on the go, the BSI-approved ECOS SecureBootStick comes into play. It then ensures highly secure, protected access to the video conference from an encapsulated environment. At the same time, a complete separation between business and private use is guaranteed - an important aspect, for example, when using a private computer in the home office.
Hybrid working models have become indispensable
"Since the beginning of the corona pandemic, video conferences have become one of the most important means of communication in many companies and authorities. And in the long term, especially in view of hybrid work models with a mix of face-to-face work and home office, they will be indispensable ”, says Paul Marx, Managing Director of ECOS Technology GmbH. “In the absence of alternatives, the usual standard solutions were often resorted to in the beginning, which, however, sometimes involve considerable security risks. With the ECOS SecureConferenceCenter, highly secure video conferences can now be easily implemented without having to forego familiar features and options. "
More at ECOS.com
About ECOS Technology
ECOS Technology GmbH has specialized in the development and sale of IT solutions for highly secure remote access as well as the management of certificates and smart cards. The core products that are used in a wide variety of industries include the ECOS SECURE BOOT STICK and the PKI appliance ECOS TRUST MANAGEMENT APPLIANCE. Companies, authorities and organizations are thus able, for example, to create, extend or withdraw their own certificates, to connect employees in the home office, to provide quickly usable, cost-efficient emergency workplaces for crises or to maintain industrial plants remotely safely and securely.