SearchLight with new Vulnerability Intelligence module. Monitoring solution from threat intelligence provider Digital Shadows enables CVEs to be prioritized for faster triage and mitigation.
Cyber threat intelligence provider Digital Shadows has added a new vulnerability analysis capability to its SearchLightTM solution. The Vulnerability Intelligence module enables security teams to identify relevant CVEs (Common Vulnerabilities and Exposures) more quickly and effectively prevent exploits.
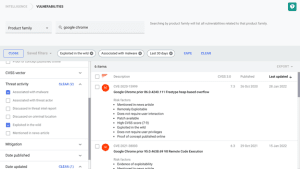
SOCs: Identify relevant CVEs faster
The module in SearchLight is based on data from nine years of intensive research and analysis by Digital Shadows' forensic threat intelligence team. The analysts continuously monitor criminal forums, gather information and document tactics, techniques and procedures (TTPs) used by attackers to exploit known vulnerabilities. The vulnerability database is supplemented by automated monitoring of code repositories, paste sites, social media, manufacturer websites and advisories. This creates a comprehensive context for evaluating risks, attack targets and possible exploits. Dedicated analysts examine the collected data, remove "white noise" and evaluate each event in terms of its criticality and relevance.
Analysis of vulnerabilities
The precise analysis of vulnerabilities simplifies the daily work of security teams in several ways. On the one hand, users can specifically search for technologies in their IT portfolio, check for possible exploits and risks and thus set mitigation priorities. On the other hand, security experts receive comprehensive context information in CVE profiles in order to optimize their reactions to high-risk vulnerabilities. Lists of up to tens of thousands of CVEs can be ranked by priority, recency, and relevance. Paste & Copy functions can also be used to create ranking lists of vulnerabilities that are of particular importance to companies.
"Enterprises have hundreds, if not thousands, of different IT assets and receive tens of thousands of vulnerability reports each year," said Russell Bentley, vice president of product at Digital Shadows. “IT security lacks the resources to filter this flood of data, let alone test and apply all the patches. Companies therefore often blindly rely on the CVSS (Common Vulnerability Scoring System). That's a good basis. However, the information contained there is purely hypothetical and does not say anything about whether there is a real risk for companies.”
Vulnerability Intelligence module
Alastair Paterson, Co-Founder and CEO: “The Vulnerability Intelligence module in SearchLight creates clarity and allows companies to focus on what is important to them. Rather than relying on a vendor's arbitrary risk assessment, security teams can now filter for specific factors. The information is no longer purely theoretical, but is based on current threat intelligence and is displayed in CVE profiles at a glance.”
More at DigitalShadows.com
About digital shadows
Digital Shadows tracks down unintentionally public data in the open, deep and dark web and thus helps organizations to reduce the resulting digital risks of external threats to a minimum. SearchLight ™ helps companies comply with data protection regulations, prevent loss of intellectual property, and prevent reputational damage. The solution helps to minimize digital risks, reduce the attack surface and protect brand and company names.