
The attacks on the VMware ESXi never end. They continue to threaten tens of thousands of servers and require updating to the latest VMware ESXi version, according to Bitdefender experts. Even rescue scripts no longer work because the ransomware has adapted.
The attacks on the VMware ESXi hypervisors, which exploit the recently discovered CVE-2021-21974 vulnerability with little effort to play a wide variety of payloads as remote code, have enormous potential for spreading. They are therefore developing into mass attacks for opportunistic cybercriminals and are a current example of hybrid attacks:
VMware-ESXi : example of hybrid attack
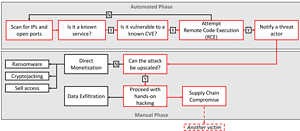
🔎 Hybrid attacks: After an automated start, the attackers switch to manual work (Image: Bitdefender).
In the first phase, the hackers proceed automatically, then evaluate search results and, in the second phase, continue to play out the targeted attack manually. It is to be expected that many users will use the vulnerability for supply chain attacks to attack the company actually notified via its suppliers.
The extent of the attacks cannot yet be precisely estimated. The attack wave is only starting now. However, the numerical potential of affected systems is enormous. According to the search results of the Shodan tool, which is openly available and also used by hackers, the number of users of a VMware ESXi host is in the tens of thousands. Up to 7.0 hosts are visible on the Internet, especially from the old versions before ESXi 60.000. The OpenSLP service, which opens up the security gap, is only deactivated by default from version 7.0 onwards. OpenSLP is also an ideal gateway for hypervisor takeover after any virtual machine has been hijacked.
Furthermore, 60.000 vulnerable ESXi 6.x servers
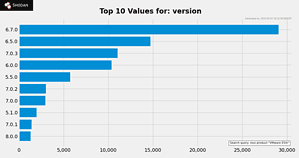
🔎 The Shodan scan tool finds over 60.000 vulnerable VMware ESXi servers in one search query (Image: Bitdefender).
“Anyone who wants to protect themselves must therefore now take basic defensive measures. And that can only be updating to the latest versions of hypervisors. The general blocking by a firewall of port 427 (TCP/UDP), which OpenSLP uses for its communication, cannot prevent a hacker from directly attacking a virtual machine. Although it is the first line of defense, it does not provide any real security. And the waves of attacks now observed are only a harbinger of more attacks this year by experienced and advanced cybercriminal groups,” said Martin Zugec, Technical Solutions Director at Bitdefender.
More at Sophos.com
About Bitdefender Bitdefender is a leading global provider of cybersecurity solutions and antivirus software, protecting over 500 million systems in more than 150 countries. Since it was founded in 2001, the company's innovations have consistently ensured excellent security products and intelligent protection for devices, networks and cloud services for private customers and companies. As the supplier of choice, Bitdefender technology is found in 38 percent of security solutions deployed around the world and is trusted and recognized by industry experts, manufacturers and customers alike. www.bitdefender.de
