In an analysis, Bitdefender warns of a series of ProxyNotShell/OWASSRF attacks targeting on-premise Microsoft Exchange installations. The attack often even ends in taking over the server. A technical guide from Bitdefender offers help.
The attacks observed since the end of November 2022, especially in the USA, served different purposes. Server-Side Request Forgery (SSRF) attacks enable opportunistic attacks via a vulnerable server on another server and can lead to the complete takeover of a Microsoft Exchange server, for example. Vulnerabilities in such high-level architectures are rarely found. If present, they are difficult to close in productive systems. This applies above all to widespread software for which backwards compatibility plays an important role - such as Microsoft Exchange.
Intelligent server takeover attacks
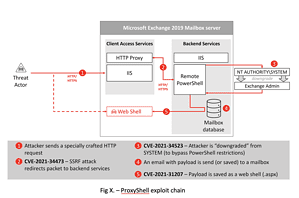
SSRF attacks are a common way to attack backend services programmed with Server Orientated Architecture (SOA) that do not have hard-coded security. The frontend proxies are responsible for their protection. In one of the attacks, the cybercriminals attacked the Client Access Services (CAS) as proxy protection on a Microsoft Exchange 2019 mailbox server. The hackers send a request through a vulnerable system, the CAS proxy authenticates the attackers' request and grants the attackers SYSTEM access to backend services (see image).
Microsoft Exchange is an ideal target for such attacks because it relies on a set of front-end and back-end services that are difficult to change due to backwards compatibility. The backend services trust a request from the front end CAS layer. Various backend goals run through the SYSTEM account. The Remote PowerShell (RPS) offers a lot of Power Shell commands.
First the server, then your own remote tools
Hackers attack such a worthwhile target for various purposes: For example, they wanted to install tools for remote access. A persistent presence on the compromised system via web shell programs should enable various actions. Hackers use the attack called ProxyNotShell to execute PowerShell commands - presumably intended to install ransomware. The capture of access data in another variant is also used to start ransomware attacks.
Defending against such attacks requires a layered cyber defense with prevention, detection and mitigation capabilities. This also includes patch management, which is not just limited to Windows, but to all applications and services with Internet access. Checking the reputation of IP addresses and URLs is also important. Defense solutions must also be able to detect fileless attacks.
More at Bitdefender.com
About Bitdefender Bitdefender is a leading global provider of cybersecurity solutions and antivirus software, protecting over 500 million systems in more than 150 countries. Since it was founded in 2001, the company's innovations have consistently ensured excellent security products and intelligent protection for devices, networks and cloud services for private customers and companies. As the supplier of choice, Bitdefender technology is found in 38 percent of security solutions deployed around the world and is trusted and recognized by industry experts, manufacturers and customers alike. www.bitdefender.de