Malwarebytes releases its June Ransomware Report. As in the previous month, LockBit remains by far the most widespread ransomware. After that come But there are also new developments. Karakurt, Black Basta, ALPHV or BlackCat.
The Malwarebytes Threat Intelligence Team attributed 44 attacks to the LockBit ransomware group in June 2022 (compared to 73 attacks in May 2022). LockBit was followed in June by Karakurt with 27 attacks, Black Basta with 18 attacks and ALPHV (aka BlackCat) with 15 attacks. Conti no longer takes up a place in the analysis in June. However, the month was also notable for the disappearance of this ransomware group, as well as a large number of attacks by groups allegedly connected to Conti.
Conti is now gone
Looking at the distribution of ransomware attacks by country, in June 2022, as in the previous month, the USA was by far the most affected country: Malwarebytes associates 70 attacks with the United States. 11 attacks occurred in the UK, 10 attacks in Canada and 9 attacks each in Germany and Italy.
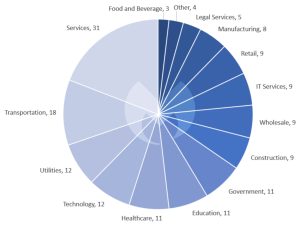
As for industries, as in May, the service sector was the most affected: According to Malwarebytes, this sector accounted for 31 attacks. In second place is Transportation with 18 attacks, followed by Utilities with 12 attacks.
LockBit: Dominant force in ransomware
Without making a big splash, LockBit has become the dominant force in ransomware this year. Even though fewer victims were published on its leak website in June than in May, the ransomware was still far ahead of its competitors.
While Conti has spent 2022 making loud statements and pulling itself out of a self-made hole with its plan to fake its own dissolution, LockBit has been fully focused on its business. LockBit is offered as ransomware-as-a-service (RaaS). The attacks are carried out by partners called "pen testers," who pay the LockBit organization 20 percent of the ransom money purchased in return for using the LockBit software and services.
LockBit advertises “We are Dutch – not Russians”
And while some ransomware gangs primarily want to generate publicity, LockBit seems more interested in what its users think. The partner site begins with a statement intended to set the company apart from its Russian rivals in particular: "We are based in the Netherlands, completely non-political and only interested in money."
Otherwise, the website is full of wording intended to signal the ransomware group's trustworthiness and willingness to listen to partners. For example, members are asked, "If you don't find one of your favorite features here, please let us know." It goes on to say, "We have never cheated on anyone and always honor our agreements." This combination of partner attractiveness and the ability to Avoiding costly mistakes seems to be the reason behind LockBit's success this year.
LockBit 3.0 including a new Darknet page
Despite this, LockBit made headlines in June 2022. The ransomware group launched LockBit 3.0 along with a new website on the dark web and a bug bounty program. The latter promised rewards of up to $XNUMX million for finding vulnerabilities in LockBit's website and software, submitting brilliant ideas, or successfully doxing the head of the LockBit affiliate program.
Whether LockBit has any serious intention of paying out these sums remains to be seen. However, should the group actually intend to use the bug bounty to improve their software and refine their practices, they could rob law enforcement and security researchers of valuable information.
Conti: Leak website disappeared in June
As expected, Conti's leaked website disappeared in June - after a few weeks of inactivity. As the Malwarebytes threat intelligence team reported back in May, research by Advintel last month indicated that the group's rapprochement with the Russian state had prompted victim lawyers to warn them against paying a ransom. Because these could have led to sanctions.
As the group's revenue dried up, Conti leaders reportedly hatched a plan to retire the brand. They divided their members into other ransomware groups like Black Basta, BlackByte, Karakurt, Hive, and ALPHV and faked their own deaths. The Malwarebytes Threat Intelligence Team was able to confirm that Conti sent an internal announcement to its members about its withdrawal at the end of May and that internal chat servers went down around the same time. The leaked website disappeared on June 22, 2022 and is still unavailable.
BlackBasta replaces Conti
Conti's shutdown coincided with the sudden emergence of Black Basta in April, as well as a surge in activity and the emergence of a new Karakurt leak website in June. It may be a coincidence, but the Malwarebytes Threat Intelligence Team found that the combined activity of Black Basta, BlackByte, and Karakurt reached levels similar to that of Conti over the past month.
Trends: Targeting customers and employees directly for the first time
The features, or even the way in which ransomware is distributed and deployed, vary little from one ransomware group to another and evolve only slowly. Therefore, the biggest innovations in recent years seem to lie in how ransomware groups do business and how they put pressure on their victims to collect ransoms.
In June, the Malwarebytes Threat Intelligence Team observed a few things that had not previously been observed: For example, as described earlier, the LockBit group was offering bounties for bugs. For the first time, the ALPHV Group addressed employees and customers of a hotel with a leaked website.
Company executives targeted
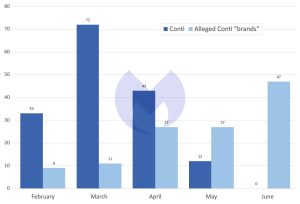
🔎 Known attacks by Conti compared to known attacks by Black Basta, BlackByte and Karakurt, February-June 2022 (Image: Malwarebytes).
Ransomware groups have already attempted to target corporate executives to increase the pressure. But the fact that ALPHV addressed employees and customers, in this case hotel guests, with a special website is new. The latter was not on the dark web but on the public internet. The website allowed guests and staff to search through 112GB of personal information stolen by ALPHV in the attack to see if their personal information was among it. This new tactic was apparently intended to put further pressure on the hotelier to pay the ransom.
By putting the site on the public web, ALPHV made the information much more accessible to non-technical users. However, the site was only available for a few days before it was taken down. The Malwarebytes Threat Intelligence Team believes the ransomware group certainly knew this was going to happen. Presumably, however, the website only had to exist long enough to attract enough attention to influence the negotiations in this way.
ALPHV advertised with user help
Such innovations are nothing new. Ransomware groups are constantly experimenting with new ideas. The experiments that don't work are forgotten. And those that work are quickly copied by other groups. In this case, the experiment does not seem to have been successful. The victim has now appeared on the ALPHV main page on the dark web. This usually indicates that it resisted pressure to pay a ransom.
More at Malwarebytes.com
Via Malwarebytes Malwarebytes protects home users and businesses from dangerous threats, ransomware and exploits that are undetected by antivirus programs. Malwarebytes completely replaces other antivirus solutions in order to avert modern cybersecurity threats for private users and companies. More than 60.000 companies and millions of users trust Malwarebyte's innovative machine learning solutions and its security researchers to avert emerging threats and eliminate malware that antiquated security solutions fail to detect. You can find more information at www.malwarebytes.com.