
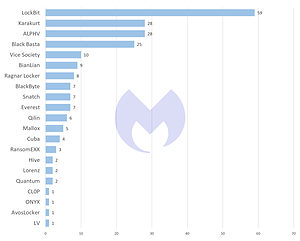
LockBit remains the leader among groups selling ransomware-as-a-service (RaaS) in October. This is what the Malwarebytes ransomware report for October shows. Even the dangerous groups Black Basta or ALPHV do not attack companies so en masse.
Malwarebytes' threat intelligence team attributed 59 attacks to the LockBit ransomware group in the last month (compared to 109 attacks in September 2022 and 62 attacks in August 2022). Karakurt and ALPHV land in second place in October, with 28 attacks each. Black Basta takes third place with 25 attacks.
LockBit replaces Conti from the top
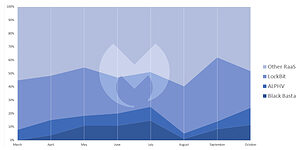
Since the disappearance of Conti, LockBit has remained the most used form of RaaS based on the attacks known to Malwarebytes. A comparison with LockBit's closest competitors is also instructive here, since since March neither ALPHV nor Black Basta has reached even remotely the same level of activity as LockBit. The latter ransomware group accounted for almost half of all RaaS activity in September 2022, accounting for 48 percent of attacks detected by Malwarebytes.
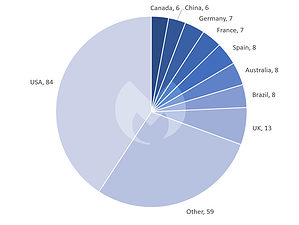
More ransomware attacks in the US than Europe
When it comes to the distribution of ransomware attacks by country, the USA is again by far the most common target in October 2022 with 84 attacks. The following European countries were also affected: the United Kingdom with 13 attacks, Spain with 8 attacks, and France and Germany with 7 attacks each.
LockBit and Continental put data up for sale for $50 million
In Germany makes LockBit is currently a hot topic in connection with a hacker attack on Continental in August. A chat between Continental and the ransomware group was recently published on their dark web website, depicting a negotiation between the two parties. The chat log shows that Continental was looking for evidence that LockBit actually had the allegedly stolen 40 TB of internal data and would ultimately delete it as soon as the ransom was paid.
The latest message, attributed to Continental and dated October 24, reads: "Hello, we have a management meeting to hold and will get back to you tomorrow at the end of the working day."
Apparently the meeting didn't go as LockBit had hoped. After several unsuccessful attempts to restart negotiations, the ransomware group has made Continental data available for sale or destruction on its dark web site for $50 million.
Money Laundering: How LockBit transfers money
An interview published by vx-underground in October provided interesting insights into the organization of LockBit. This was allegedly conducted with LockBit's founder, referred to on the site as "LockBit administrator" (LBO). The interview sheds light on the size of LockBit and also how ransoms paid in cryptocurrency are converted into cash.
First, regarding the size of the LockBit organization, according to LBO, LockBit currently has over 10 members consisting of pentesters, developers, money launderers, testers, and negotiators. This would make the LockBit team almost an order of magnitude smaller than that of Conti, which consisted of around 100 members before it was dissolved.
Ultimately, the scalability of RaaS comes from the use of affiliates – that is, partner organizations that carry out attacks with LockBit ransomware and pay for this with part of the ransom. According to LBO, LockBit currently has no more than 100 affiliates, the wish would be 300.
A lot of money spread over a few heads
According to Malwarebytes figures, these 100 people are responsible for about a third of all RaaS attacks. This suggests that the number of professional criminals involved in ransomware attacks is likely to be small. However, considering the enormous sums of money that have been extorted from ransomware groups over the past five years and have thus flowed into relatively few hands, one can assume that this must be a considerable financial transaction.
According to LBO, the ransom will be sent to Chinese money changers, and from there to another money changer. The money is then transferred to bank cards using a variety of methods. Money couriers are then sent to ATMs and ultimately bring the money to LockBit. Transfers range from $1.000 to $7.000.
According to the Ransomware Task Force, ransomware victims paid a total of $2020 million in ransoms in 350. The use of money laundering techniques as described above would thus require at least 50.000 ATM transactions. This could be a clue as to why cryptocurrency transfers and money laundering seem to be top law enforcement targets over the past two years.
LockBit clones surfaced in October
In September, the software builder for LockBit 3.0 was released. Malwarebytes' threat intelligence team found that creating your own ransomware has never been easier. In addition, Malwarebytes predicted that new criminal gangs not previously affiliated with LockBit could use the software in the future - including to create their own ransomware outside of the LockBit affiliate program.
This actually happened in October. There are suspicions that the Bl00dy ransomware group used the LockBit 3.0 builder (note: since Bl00dy did not publish any leaks on the dark web in October, the group does not appear in the October chart of known ransomware attacks by groups). A LockBit clone was rumored to have been used in an attack on Banco de Brasília (BRB). And a bitcoin address discovered in ransom notes from an unknown group using modified LockBit software has received about $20.000 in payments.
Malwarebytes' October 2022 ransomware report includes even more analyzed data. It is available to read online for free. A click on the button leads directly to the report.
More at Malwarebytes.com
Via Malwarebytes Malwarebytes protects home users and businesses from dangerous threats, ransomware and exploits that are undetected by antivirus programs. Malwarebytes completely replaces other antivirus solutions in order to avert modern cybersecurity threats for private users and companies. More than 60.000 companies and millions of users trust Malwarebyte's innovative machine learning solutions and its security researchers to avert emerging threats and eliminate malware that antiquated security solutions fail to detect. You can find more information at www.malwarebytes.com.

One thought on "Ransomware Report: LockBit remains the most dangerous"
Comments closed