
There is still no official confirmation of a LockBit hacking attack on Continental. If the chat log on the LockBit leak page is genuine, then the transfer of 40 TB of data was negotiated. According to the hacker, the pure file list of the data alone should have a volume of 8 GB.
A chat log was recently found on the LockBit page. At some point, whoever was chatting with the LockBit hackers simply stopped responding. First, however, there was a conversation in which the hacker talked about the data and the unknown negotiator - perhaps commissioned by Continental - wanted to have proof of the captured data. According to the chat, the hacker then compiles a file list for him and offers to send him a special link. However, that would take time, since the file and directory list would already be a file with 8 GB.
The chat just breaks off
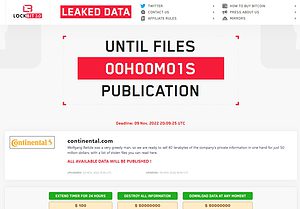
🔎 Build pressure: The LockBit counter expires and wants to display data. Only Continental knows whether these are genuine (Image: B2B-CS).
At some point, the hacker's counterpart simply stops responding. The hacker kept threatening to publish the data in the chat and urged the ransom to be paid. But there was no further reply from the other side. Meanwhile, the leak site indicated that LockBit will publish the data. But the hackers have not given up completely. While the countdown continues, there are buttons under the clock to extend the countdown. Only $100 is enough for another 24 hours. Furthermore, the data is offered for download for 50 million dollars or for deletion for 50 million dollars.
As evidence, the hackers show 4 screenshots that are said to come from the data collection; It's probably about car equipment. Although the note “Confidential” can be found on some screens, it cannot be said whether the data is genuine. Whether it really is 40 TB of data from Continental remains open.
The countdown is running out
Shortly after the counter expired, the LockBit leak page flipped and showed the note “Files are published”. However, no other files were visible at first. The page keeps showing new countdowns, but no data. This is how you want to keep the pressure on Continental. However, the blackmailers have had no success so far. Continental's behavior in not paying for the attack is spot on according to most experts, as this article shows.
Gateway to former attack?
“The ransomware attack on Continental is another example of why taking the simple step toward containment of security breaches is so important. Even if organizations think they've stopped ransomware in one area, they can't guarantee that it hasn't already spread to other parts of the organization. Detection and response alone are not enough, we are now in a time where containment of security breaches is the top priority.
Ransomware is more pervasive than ever - our study shows that 79% of German businesses have been hit by a ransomware attack - yet as a nation we are still too focused on preventing or thwarting attacks. It is clear that we will never be able to prevent and detect all attacks, so security practices must evolve to increase resiliency. That means we need to be prepared for security breaches and employ technology to mitigate the impact of attacks.” According to Alexander Goller, Senior Systems Engineer at Illumio.
