
The Brand Phishing Report shows which brands are most commonly impersonated to steal personal or payment information. Microsoft, Google and Apple are currently the top three most imitated brands.
In Q2023 2023, global technology company Microsoft climbed the Brand Phishing Report rankings, moving up from third place in Q29 19 to first place. The tech giant accounted for 5 percent of all phishing attempts. This could be partly due to a phishing campaign where hackers targeted account holders with deceptive messages about unusual activity on their account. According to the report, Google was second with XNUMX percent of all attempts, and Apple third with XNUMX percent of all phishing incidents. In terms of sectors, the technology sector was the most affected, followed by banks and social networks.
Check emails carefully
“While the most counterfeited brands change from quarter to quarter, cybercriminals' tactics hardly change. That's because the method of flooding our mailboxes and luring us into a false sense of security by using legitimate logos has proven successful time and time again," said Omer Dembinsky, data group manager at Check Point Software Technologies. "That's why we all need to take a moment before we click on a link we don't recognize. Does anything strike us as odd? Is the grammar bad, or is the diction odd? If so, then this could be an indication of a phishing email. For organizations concerned about their own data and reputation, it is important that they use the right technologies to effectively block these emails before they have a chance to fool a victim.”
Criminals fake websites of well-known brands
In a brand phishing attack, criminals try to impersonate the official website of a well-known brand by using a similar domain name or URL and web design that resembles the real website. The link to the fake website can be sent to the targeted individuals via email or text message. It is also possible that a user could be redirected while browsing the web or from a rogue mobile application. The fake website often includes a form designed to steal users' login details, payment details, or other personal information.
Top Phishing Brands in Q2 2023
Below are the top brands by their overall appearance in branded phishing attempts:
1. Microsoft (29 percent)
2. Google (19,5 percent)
3. Apple (5,2 percent)
4. Wells Fargo (4,2 percent)
5. Amazon (4 percent)
6. Walmart (3,9 percent)
7. Roblox (3,8 percent)
8. LinkedIn (3 percent)
9. Home Depot (2,5 percent)
10. Facebook (2,1 percent)
Microsoft phishing emails - example of unusual activity
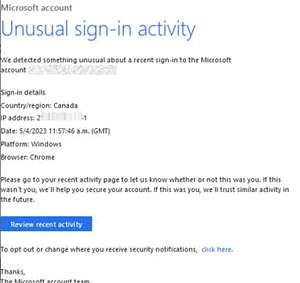
🔎 Fake mail, allegedly from Microsoft, asking the user to check recent activity (Image: Check Point)
In Q2023 XNUMX, a phishing campaign targeted Microsoft account holders by sending deceptive messages about unusual sign-in activity. The campaign included bogus emails allegedly coming from within the company with sender names such as "Microsoft (at) ' were sent. The senders claimed to have detected unusual sign-in activity in the recipient's Microsoft account. The emails contained details of the alleged login, such as country/region, IP address, date, platform, and browser.
To address these perceived security concerns, the phishing emails asked recipients to check their recent activity by clicking on a link that leads to malicious, non-Microsoft websites. The URLs used in the campaign are not currently accessible, but are believed to be aimed at stealing user credentials and personal information, or downloading malicious content onto the user's device.
To protect yourself from phishing, Check Point offers the following tips:
Check web addresses: An easy way to spot phishing attacks is to look for mismatched email addresses, links, and domain names. Recipients should always hover over a link in an email before clicking to see the link's actual destination. If the email claims to be from Microsoft, but the email address's domain is not "microsoft.com", this is a sign of a phishing email.
Check for HTTPS: For each link, make sure the website includes "HTTPS" in the URL. This means that the website has an SSL certificate. This means that the data you enter is encrypted and secure. The green padlock in the address bar also indicates this.
Implement advanced security measures, which consider more than one indicator, to determine if an email is clean or not.
Ask the IT department, if they are unsure about the legitimacy of an email.
More at CheckPoint.com
About check point Check Point Software Technologies GmbH (www.checkpoint.com/de) is a leading provider of cybersecurity solutions for public administrations and companies worldwide. The solutions protect customers from cyberattacks with an industry leading detection rate for malware, ransomware and other types of attacks. Check Point offers a multi-level security architecture that protects company information in cloud environments, networks and on mobile devices, as well as the most comprehensive and intuitive “one point of control” security management system. Check Point protects over 100.000 businesses of all sizes.
