
The use of macros to spread malware has declined significantly: by as much as 2021 percent between October 2022 and June 66. However, attackers are beginning to use tricks to circumvent the protection.
Commonly, cyber criminals use VBA macros to automatically execute malicious content if a user has macros enabled in Office applications. XL4 macros, on the other hand, are specific to the Excel application, but can also be used by attackers as a tool for spreading malware. The masterminds behind macro-based attacks typically use social engineering to convince the recipient that the content is important and therefore enabling macros is required to view that content.
Containers like ISO, LNK and RAR as a trick
“The fact that cybercriminals are increasingly abandoning the direct distribution of macro-based file attachments in emails represents a significant change in the threat landscape. Attackers are instead using new tactics to distribute malware. It can be expected that the increasing use of file types such as ISO, LNK and RAR will continue,” commented Sherrod DeGrippo, vice president of threat research and detection at Proofpoint.
Circumvention of security functions
Microsoft blocks VBA macros that have a Mark-of-the-Web (MOTW) attribute. This attribute indicates whether a file comes from the Internet and is based on what is known as a Zone.Identifier. Microsoft applications add this attribute to certain documents when they are downloaded from the Internet.
However, cyber criminals can use container file formats such as ISO (.iso), RAR (.rar), ZIP (.zip), and IMG (.img) to evade this MOTW-based security feature. Once downloaded, the container files are tagged with the MOTW attribute since they were downloaded from the Internet, but the document they contain, such as a macro-enabled spreadsheet, is not tagged with the attribute. When the document is extracted, the user still needs to enable macros for the malicious code to run automatically, but the file system will not identify the document as coming from the Internet.
It is also possible for attackers to use container files to directly propagate a malicious payload. For this purpose, container files can contain additional content such as LNKs, DLLs or executable files (.exe) that lead to the installation of such a payload.
Significant changes in the threat landscape
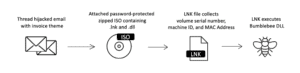
This is what the attack chain looks like to distribute the Bumblebee malware via ISO (image: proofpoint).
Proofpoint's research found a significant decrease in macro-enabled documents sent as email attachments as part of attacks. Between October 2021 and June 2022, their number decreased by more than two thirds. During the same period, the number of campaigns using container files and Windows Shortcut (LNK) attachments increased by nearly 175 percent.
This increase is partly due to the growing use of ISO and LNK files in cyber campaigns. Cyber criminals are increasingly using these as initial access mechanisms, such as those behind the Bumblebee malware attacks. The use of ISO files alone grew by over 2021 percent between October 2022 and June 150. In fact, the number of campaigns that included LNK files has increased by as much as 2021 percent since October 1.675.
More at proofpoint.com
About Proofpoint Proofpoint, Inc. is a leading cybersecurity company. The focus for Proofpoint is the protection of employees. Because these mean the greatest capital for a company, but also the greatest risk. With an integrated suite of cloud-based cybersecurity solutions, Proofpoint helps organizations around the world stop targeted threats, protect their data, and educate enterprise IT users about the risks of cyberattacks.
