
Check Point security researchers are observing a new type of phishing attack that uses a dangerous QR code. The new “quishing” is becoming more and more prevalent as many users scan the codes without hesitation.
The new variant of phishing with QR codes is becoming increasingly popular: quishing or QR code phishing. The actually harmless QR codes are ideal for disguising malicious intentions. A common QR code image can hide a malicious link, which is hardly visible. Since users are used to QR codes, such a code in an email is often not recognized as a threat. For this reason, security researchers recommend paying close attention to the sender if an email contains a QR code. If in doubt, it is better to go to the respective website directly.
Dangerous emails with QR code
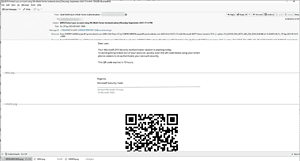
🔎 The email showed a phishing attack with a QR code (quishing) - of course it didn't come from Microsoft (Image: Check Point).
The picture below shows a specific attack. The hackers created a QR code that leads to a page where login information is collected. The alleged reason is that Microsoft multi-factor authentication is expiring and you should therefore authenticate yourself again. Contrary to the text's claim that it comes from Microsoft Security, the return address belongs to another source.
Once the user scans the QR code, they are redirected to a page that looks like Microsoft's website, but is actually just designed to steal their credentials. The attack works like this: An image with the text is created to bypass some speech analysis tools.
Security should be able to use OCR
Optical character recognition (OCR) is often used as a countermeasure. OCR converts images into text to make it readable. However, the hackers have found another way to get around this, namely a QR code. Combating these attacks is more complicated. The OCR within the protection solution must have a built-in QR code recognition function in which the URL is translated and analyzed by URL analysis tools.
You can't always know which direction the hackers will go next. However, defenders have basic tools to combat them, such as following inline encryption procedure as well as URL wrapping and emulation tools, or opening encryption.
More at CheckPoint.com
About check point Check Point Software Technologies GmbH (www.checkpoint.com/de) is a leading provider of cybersecurity solutions for public administrations and companies worldwide. The solutions protect customers from cyberattacks with an industry leading detection rate for malware, ransomware and other types of attacks. Check Point offers a multi-level security architecture that protects company information in cloud environments, networks and on mobile devices, as well as the most comprehensive and intuitive “one point of control” security management system. Check Point protects over 100.000 businesses of all sizes.
