
A survey shows the fatal misconception about the duration between a cyber attack and recognizable effects: Many employees in Germany believe that the effects of a cyber attack become apparent within a week, for example through data encryption followed by a ransom demand.
Cyber criminals spy on company data, read communications and gain access to systems via employees or weak points. They usually act in secret for a long time and remain unnoticed for months. However, every second employee in Germany thinks that a cyber attack can be identified after a few days and that the time from an attack to noticeable signs of an IT security incident is one week.
Misconception: attack noticed after a week
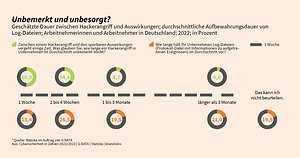
🔎 More than half of employees believe that the effects of a cyber attack will become apparent within a week (Image: G DATA).
This is the result of the exclusive "Cybersecurity in Numbers" survey by G DATA CyberDefense, Statista and brand eins. A mistake, because encrypted systems with a ransom demand are only the visible tip of the iceberg. As soon as criminals move in a company's network, they leave traces, for example in log files. These contain automatically logged information about actions and processes on a computer system. As long as there is no continuous monitoring and evaluation, these traces remain undetected and prevent early intervention.
Detect tracks of criminals in time
Another survey result: two out of five companies keep log files between one and four weeks. Every fifth respondent does not know how long log files are stored. They play an important role in the early detection of cyber attacks or in IT forensics. A short retention time, a lack of specialist staff and insufficient specialist knowledge in the field of IT security make it difficult for IT departments to identify suspicious or harmful processes in log files at an early stage and to ward off attacks before greater damage occurs.
Companies are therefore dependent on external service providers and corresponding solutions, such as Managed Endpoint Detection and Response (MEDR), to detect and stop cyber attacks at the slightest sign. IT specialists can identify anomalies in systems at an early stage by continuously monitoring the IT systems and, for example, continuously evaluating log files.
Study "Cyber Security in Numbers"
The study "Cyber Security in Numbers" is characterized by a high density of information and particular methodical depth: More than 5.000 employees in Germany were surveyed as part of a representative online study on cyber security in the professional and private context. The experts from Statista conducted the survey and, thanks to a sample size that is well above the industry standard, they are able to present reliable and valid market research results in the "Cyber Security in Numbers" booklet.
More at GData.de
About G Data With comprehensive cyber defense services, the inventor of the anti-virus enables companies to defend themselves against cybercrime. Over 500 employees ensure the digital security of companies and users. Made in Germany: With over 30 years of expertise in malware analysis, G DATA conducts research and software development exclusively in Germany. The highest standards of data protection are paramount. In 2011, G DATA issued a “no backdoor” guarantee with the “IT Security Made in Germany” seal of trust from TeleTrust eV. G DATA offers a portfolio from anti-virus and endpoint protection to penetration tests and incident response to forensic analyzes, security status checks and cyber awareness training to defend companies effectively. New technologies such as DeepRay use artificial intelligence to protect against malware. Service and support are part of the G DATA campus in Bochum. G DATA solutions are available in 90 countries and have received numerous awards.
