As Tenable's Threat Landscape Report shows, the most frequently attacked vulnerabilities have typically been known for many years. The attackers are counting on the fact that the patches have not been used and that no one is monitoring the gaps. With Microsoft Exchange, Log4Shell or Follina, there were always old vulnerabilities.
Tenable's annual Threat Landscape Report is out. The report confirms the continued threat of known vulnerabilities—that is, those for which patches have already been made available—as the prime vector for cyberattacks. Findings are based on Tenable Research Team's analysis of cybersecurity incidents, vulnerabilities, and trends in 2022, including analysis of 1.335 data breaches that became public between November 2021 and October 2022.
Report categorizes key vulnerability data
The Tenable Threat Landscape Report categorizes key vulnerability data and analyzes attacker behavior. The aim is to help companies inform their security officers and prioritize security measures. By focusing on the areas of greatest risk and disrupting attack vectors, organizations can reduce vulnerability to cyber incidents. The analyzed incidents affected more than 2,29 billion records, representing 257 terabytes of data. More than three percent of all data breaches identified were caused by unsecured databases, resulting in the loss of over 800 million records.
Attackers continue to find success with known and proven exploitable vulnerabilities that organizations have not successfully patched or fixed. According to the Tenable report, the top tier of most exploited vulnerabilities includes a large pool of known vulnerabilities, some of which were publicized as early as 2017. Organizations that failed to apply vendor patches for these vulnerabilities were at increased risk of attacks in 2022.
2022 Disasters: Exchange, Log4Shell, Follina
The most commonly exploited vulnerabilities within this group include several high-level vulnerabilities in Microsoft Exchange, Zoho ManageEngine products, and Virtual Private Network solutions from Fortinet, Citrix, and Pulse Secure. For the other four most commonly exploited vulnerabilities — including Log4Shell, Follina, a vulnerability in Atlassian Confluence Server and Data Center, and ProxyShell — patches and mitigations were widely released and readily available. In fact, four of the first five zero-day vulnerabilities exploited in the wild in 2022 were released on the same day that the vendor released patches and mitigation guides.
"The data shows that well-known vulnerabilities are often more damaging than new ones," said Bob Huber, Tenable's chief security officer and head of research. “Cyber attackers consistently find success in exploiting these overlooked vulnerabilities to gain access to sensitive information. Numbers like these clearly show that reactive cybersecurity measures after an incident are not enough to mitigate risk. The only way to turn the tide is to move to pre-emptive security and exposure management.”
No CVEs on cloud service provider issues
Shifting to a “cloud-first” attitude allows organizations to grow and scale, but it also introduces new risks, as cloud service providers (CSPs) often patch and security harden without notice. Vulnerabilities that affect CSPs are not reported in a security advisory, given a CVE identifier, or mentioned in the release notes. This lack of visibility makes it difficult for security teams to accurately assess risk and report back to stakeholders.
APT groups hit mercilessly
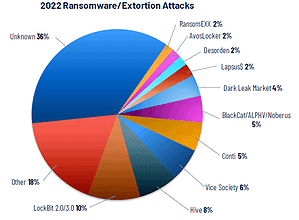
In addition to analyzing vulnerabilities and misconfigurations, the report also examines the proliferation of attack groups and their tactics. Ransomware is still the most common attack vector used in successful attacks. Previous Tenable studies found that double ransomware and ransomware-as-a-service models are fueling the multi-million dollar ransomware ecosystem. Ransomware-as-a-Service makes it easier than ever for cybercriminals who lack technical skills to commercialize ransomware.
The LockBit ransomware group is a well-known user of double and triple ransomware tactics. It dominated the ransomware space with 7,5% of analyzed ransomware incidents, followed by the Hive ransomware group (6,3%), Vice Society (5,1%) and BlackCat/ALPHV (XNUMX%).
More at Tenable.com
About Tenable Tenable is a Cyber Exposure company. Over 24.000 companies worldwide trust Tenable to understand and reduce cyber risk. Nessus inventors have combined their vulnerability expertise in Tenable.io, delivering the industry's first platform that provides real-time visibility into and secures any asset on any computing platform. Tenable's customer base includes 53 percent of the Fortune 500, 29 percent of the Global 2000, and large government agencies.