Trend Micro is expanding cooperation in the area of connected cars. In cooperation with Fujitsu, Hitachi and Microsoft Japan, Trend Micro develops cybersecurity measures for connected vehicles. However, due to their connection to the internet, intelligent vehicles are threatened by cyber attacks.
Trend Micro, one of the world's leading providers of cybersecurity solutions, is developing security solutions for connected vehicles with Fujitsu, Hitachi and Microsoft Japan. These support car manufacturers in implementing the current cyber security regulations for the industry.
Cybersecurity Regulations for Connected Cars
The market for connected vehicles is growing rapidly and data about vehicles and the traffic conditions around them is playing an increasingly important role in the development of future-proof mobility solutions. However, due to their connection to the internet, smart vehicles are exposed to the threat of cyber attacks. Therefore, continuous security and threat monitoring is required in the connected vehicles themselves, as well as across the platform, to reliably detect and respond to incidents and signs of cyber attacks. This is the only way to get a comprehensive overview of the vehicle data.
Fujitsu and Trend Micro improve the security of connected vehicles
Starting this year, Fujitsu Limited and Trend Micro are working with carmakers around the world to improve security measures for connected vehicles and their cloud infrastructure.
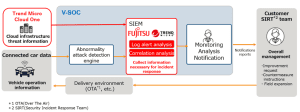
As part of the partnership, Fujitsu is providing a security solution for connected vehicles with the V-SOC service (Vehicle Security Operations Center), with Trend Micro Cloud One, the comprehensive cloud security platform from the Japanese IT security provider, complementing the backend cloud -Infrastructure protects. Both solutions work together to detect anomalies in the vehicle. These include, for example, malfunctions of the accelerator pedal or the brakes. In addition, they offer additional detection functions for unauthorized communication and attempts to manipulate telematics servers and security data in the cloud infrastructure. The individual elements are recorded and analyzed holistically.
Visualization of potential cyber attacks
The new services enable the visualization of a comprehensive picture of potential cyber attacks. Because they detect threats that emanate from the cloud infrastructure, which is attractive to cybercriminals, and also link these detection functions with warnings in the vehicle. The services can also be used to determine the starting points of threats and the effects of cyber attacks. This makes it possible to initiate appropriate security measures.
Hitachi, Microsoft Japan and Trend Micro join forces to protect connected cars
A solution capable of monitoring and securing many vehicles in use around the world against the ever-increasing number of attacks requires careful coordination between cloud security, IT systems and automotive infrastructure. Hitachi's vehicle and IT solutions, Trend Micro's vehicle and cloud security solutions and threat intelligence and, moreover, Microsoft's cloud platform together form a holistic solution for connected vehicles. This also includes security solutions in connected cars that detect, analyze and combat cyber attacks on vehicles and peripheral systems. The jointly developed solution is to be rolled out to automobile manufacturers and suppliers in Japan by the end of the year and then be available globally.
The following services are provided as part of the cooperation:
- Detect and prevent cyber attacks and risks to vehicles
- Providing a powerful and secure cloud platform
- Visualization of a comprehensive overview of cyber attacks in connection with vehicle data
Learn more about cybersecurity regulations
Currently, automotive cybersecurity regulations are based on the United Nations Economic Commission for Europe (UNECE) World Forum for Harmonization of Vehicle Regulations (WP.29) working party. . The WP.29 regulation outlines the need for a system to collect, monitor and analyze threat intelligence both inside and outside the vehicle to enable autonomous driving. Vehicle manufacturers around the world are implementing countermeasures based on this guide.
In addition, Trend Micro published a study on cyber security in connected vehicles. This supports manufacturers, suppliers, authorities and service providers in implementing the new UN regulation on cyber security for connected vehicles. It also analyzes cyber risks that are not yet taken into account in the current requirements. The full report "Identifying Cybersecurity Focus Areas in Connected Cars Based on WP.29 UN R155 Attack Vectors and Beyond' is available online in English.
More at TrendMicro.com
About Trend Micro As one of the world's leading providers of IT security, Trend Micro helps create a secure world for digital data exchange. With over 30 years of security expertise, global threat research, and constant innovation, Trend Micro offers protection for businesses, government agencies, and consumers. Thanks to our XGen™ security strategy, our solutions benefit from a cross-generational combination of defense techniques optimized for leading-edge environments. Networked threat information enables better and faster protection. Optimized for cloud workloads, endpoints, email, the IIoT and networks, our connected solutions provide centralized visibility across the entire enterprise for faster threat detection and response.