
Since Microsoft has now blocked all macros by default, cyber attackers have been looking for new ways - and they find them. Security researchers from Proofpoint observed this and were able to gain insights into the behavior of cybercriminals.
These warps are largely due to Microsoft now blocking macros by default. All players in the cybercriminal food chain - from the small, inexperienced hacker to the most experienced cybercriminals executing large-scale ransomware attacks - are therefore forced to adapt the way they work.
No macros? There are other ways!
🔎 Since VBA and XL4 macros are blocked, attackers like Qbot are switching to other file types, like HTML smuggling or VHD (Image: Proofpoint).
Proofpoint's security researchers were able to gain valuable insights into the changing behavior of cybercriminals. As a result, attackers are now experimenting extensively with legacy file types, unexpected attack chains, and a variety of techniques to proliferate their malware payloads – including ransomware.
Proofpoint was able to make the following observations:
- Cyber criminals continue to test different approaches to find the most effective way to compromise a target via email. This shows that there is no reliable, uniform method that is used by all actors in the cybercrime ecosystem.
- As soon as a group of cybercriminals uses a new technique, it is also used by other groups of criminals in the weeks or months that follow.
- The most sophisticated cybercrime actors have the time and resources to develop and test new malware delivery techniques.
The example of the cybercriminal group TA570, also known as "Qbot", is a good illustration of how much the perpetrators now vary in their efforts to deliver malware to their potential victims.
Qbot changes its entire strategy
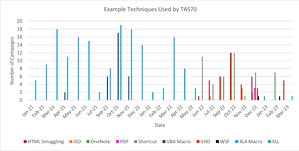
Originally, i.e. before June 2022, TA570 almost exclusively used VBA macros and XL4 macros in its campaigns to distribute malware payloads. This was usually Qbot, but also IcedID. In June 2022, Proofpoint's security researchers were able to observe the first changes. The group turned to several new Tactics, Techniques and Procedures (TTPs), most notably using HTML smuggling for the first time.
In the months that followed, TA570 resorted to new and different TTPs, using up to six different and unique attack chains and numerous file types in one month. File types included PDF, LNK, Virtual Hard Disks (VHD), ISO, OneNote, Windows Script File (WSF), and XLLs, among others.
The Proofpoint experts have compiled their findings on the disappearance of macros as an attack vector in a detailed investigation in a PDF report.
Directly to the PDF report at Proofpoint.com
About Proofpoint Proofpoint, Inc. is a leading cybersecurity company. The focus for Proofpoint is the protection of employees. Because these mean the greatest capital for a company, but also the greatest risk. With an integrated suite of cloud-based cybersecurity solutions, Proofpoint helps organizations around the world stop targeted threats, protect their data, and educate enterprise IT users about the risks of cyberattacks.
