Some attackers use online meeting services as bait for malware. Researchers at Zscaler found fake Skype, Zoom and Google Meet websites that were used by threat actors to spread Remote Access Trojans - RAT for short.
Zscaler's ThreatLabZ team warns about fake online meeting sites that distribute various malware families. Already at the beginning of December 2023, the researchers discovered a threat actor who creates fake Skype, Google Meet and Zoom websites to spread malware in order to spread remote access Trojans such as SpyNote RAT to Android users and NjRAT and DCRat to Windows users . These pages keep appearing in new versions.
Deceptively real web addresses as a trap
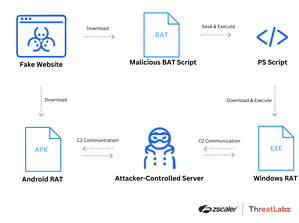
The malware actor used shared web hosting and hosted all fake websites for online meetings on a single IP address. The URLs of the fake websites were very similar to the real ones, so that the fake cannot be recognized at a glance. When a user visits one of the fake websites, clicking on the Android button will start downloading a malicious APK file. Clicking on the corresponding Windows button, however, triggers the download of a BAT file. When executed, the BAT file provides additional actions that ultimately result in the download of a RAT payload.
False websites with Skype
During their investigation, security researchers discovered that the first fake and now blocked website “join-skype[.]info” was created in early December to trick users into downloading a fake Skype application.
The Windows button pointed to a file called “Skype8.exe” and the Google Play button pointed to “Skype.apk”. The Apple App Store button only redirected to the original Skype for iOS page, indicating that the threat actor did not target iOS users with its malware.
Incorrect meeting pages for Google Meet and Zoom
At the end of December, the attacker created another fake website that imitated Google Meet. The fake Google Meet page was hosted with the “gry-ucdu-fhc” subpath visible. It was intentionally created to resemble a Google Meet join link. The experts also found a fake Zoom page for Zoom at the end of January 2024. Their URL contained a subpath very similar to a meeting ID generated by the Zoom client.
RAT – Remote Access Trojans were ready
The threat actors target companies with this campaign and use well-known and popular online meeting services as bait to spread RATs for Android and Windows. These Remote Access Trojans are capable of stealing confidential information, logging keystrokes, or siphoning files.
These findings highlight the need for robust security measures to protect against evolving threats, as well as the importance of regular updates and security patches. The Zscaler Cloud Sandbox recognizes the samples by their behavior and refers to specific MITER ATT&ACK techniques that are triggered during the analysis.
More at ZScaler.com
About Zscaler Zscaler accelerates digital transformation so customers can become more agile, efficient, resilient, and secure. Zscaler Zero Trust Exchange protects thousands of customers from cyberattacks and data loss by securely connecting people, devices, and applications anywhere. The SSE-based Zero Trust Exchange is the world's largest inline cloud security platform, distributed across 150+ data centers around the world.