
Security researcher Aaron Thacker actually just wanted to build a server out of a Cisco appliance. He discovered a vulnerability in the web-based management interface of the Cisco Integrated Management Controller. He then installed Doom and played it as a demo in the management console.
Security researcher Aaron Thacker only managed to hack a Cisco C195 Email Security Appliance, but the vulnerability affects a whole range of Cisco devices. Thacker just wanted to build a server out of the appliance and discovered the vulnerability during the conversion. He then started a chain of attacks:
- He changed the BIOS to make CIMC accessible to the network.
- He then attacked the CIMC management system over the network to gain root access to a critical component in the system via a remote command execution vulnerability (CVE-2024-20356).
- Finally, the secure boot chain could be compromised by changing the device PID to allow other secure boot keys to be used.
Vulnerability exploited – installed and played Doom
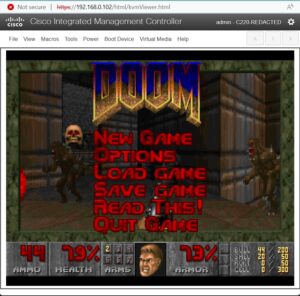
🔎 Security researcher Aaron Thacker cracked the Cisco appliance and installed Doom in the management console as a demo (Image: Aaron Thacker, Doom Copyrights by ID Software)
The researcher had of course informed Cisco in advance and set a corresponding publication date. Cisco took advantage of the time and provided appropriate updates for the entire product line. In a security statement, Cisco lists all devices affected by the vulnerability. This has a CVSS value of 8.7 out of 10 and is therefore considered highly dangerous.
Cisco calls the vulnerability “Command Injection Vulnerability in the Web-based Management Interface of the Cisco Integrated Management Controller (IMC)” A vulnerability in the web-based management interface of the Cisco Integrated Management Controller (IMC) could allow an authenticated, remote attacker with administrative privileges to conduct command injection attacks on an affected system and its Increase rights to root privileges.
This vulnerability is due to insufficient validation of user input. An attacker could exploit this vulnerability by sending crafted commands to the web-based management interface of the affected software. A successful exploit could allow the attacker to elevate their privileges to root.
Cisco provides updates
Cisco provides instructions and updates for the vulnerability with CVE identifier CVE-2024-20356 on its website. Since the vulnerability is considered highly dangerous, Cisco recommends an immediate update.
More at Cisco.com
About Cisco Cisco is the world's leading technology company that makes the Internet possible. Cisco is opening new possibilities for applications, data security, infrastructure transformation and the empowerment of teams for a global and inclusive future.
