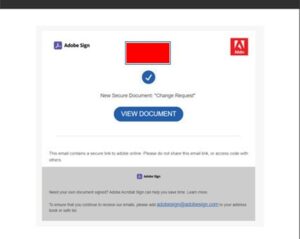
A new phishing scam is on the rise that abuses Adobe InDesign and uses it to distribute malicious links. Apparently the campaign was so successful that Barracuda saw an increase in said phishing emails from 75 to 2.000 per day.
Phishing attacks are becoming increasingly sophisticated, using various methods to evade detection and trap victims. There is currently an increase in phishing attacks that abuse Adobe InDesign, a well-known and trusted document publishing system.
Increase by a factor of 30: Phishing with Adobe InDesign links
According to Barracuda Telemetry, the number of emails containing Adobe InDesign links has increased nearly 30x since October. While the daily number was previously around 75 per email per day, it has now increased to around 2.000. Almost one in 10 (9 percent) of these emails contain active phishing links. Many of these links have the top-level domain “.ru” and are hosted behind a Content Delivery Network (CDN) that acts as a proxy for the source site. This helps obscure the source of the content and makes it harder for security technologies to detect and block the attacks.
In addition, legitimate brand logos are used in the phishing emails because they are known to the target persons and inspire trust. This suggests that the attackers invested time and resources in creating these messages. The messages ask the recipient to click on a link that will take them to another website hosted on the indd.adobe(.)com subdomain but actually controlled by the attackers to carry out the next phase of the attack .
Why these attacks are successful
The attacks that exploit Adobe InDesign use several tactics to evade detection and trick their victims:
- You use a well-known and trusted domain that is usually not blocked.
- Additionally, by using a publishing program, they can create very convincing social engineering attacks.
- As soon as the recipient clicks on the link, they will be redirected to another website. This means that there is no known malicious URL link in the body of the message that traditional security tools could detect and block.
- For attacks hosted behind the CDN, this helps obscure the malicious source of the content and makes it more difficult for security technologies to detect and block the attack.
Measures for protection
To defend against these attacks, it is important for organizations to have advanced, multi-layered, AI-powered email security capable of detecting both new and known threats. This should also include a link protection feature to ensure that users do not click on malicious URLs. The technology checks each URL at the time of click to determine whether the link is safe before allowing a redirect. As a layer of protection between email and recipient, this feature provides a critical last line of defense when threats are new or unknown.
More at Barracuda.com
Via Barracuda Networks Striving to make the world a safer place, Barracuda believes that every business should have access to cloud-enabled, enterprise-wide security solutions that are easy to purchase, implement and use. Barracuda protects email, networks, data and applications with innovative solutions that grow and adapt as the customer journey progresses. More than 150.000 companies worldwide trust Barracuda to help them focus on growing their business. For more information, visit www.barracuda.com.