Attacks on Linux systems have been increasing for several years. A provider of security solutions therefore conducted a study analyzing and comparing ransomware attacks on Linux and Windows.
Ransomware attacks on Linux systems, particularly ESXi systems, have increased significantly in recent years. That's why Check Point Research (CPR) delves into the intricacies of these incidents and draws comparisons to their Windows counterparts. Historically, ransomware threats have primarily targeted Windows environments.
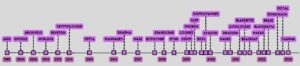
However, the malware, which aims to encrypt the data of its victims, which the attackers then usually only release again in return for large ransoms, is constantly evolving. Ransomware that targets Linux is becoming increasingly important. The CPR study analyzes 12 known ransomware families that either directly target Linux systems or have cross-platform capabilities that allow them to infect both Windows and Linux indiscriminately.
Sharp increase in ransomware attacks on Linux systems since 2021
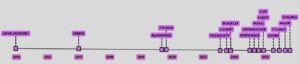
The release of Babuk source code in 2021 has played a crucial role in the spread of various ransomware families. Those aimed at Linux are characterized by their relative simplicity compared to their Windows counterparts. Many of these Linux-targeted threats rely heavily on the OpenSSL library, with ChaCha20/RSA and AES/RSA emerging as the most common encryption algorithms in the samples analyzed.
A look at historical development shows that the first identifiable example of ransomware dates back to 1989 and affected Windows systems. It wasn't until 2015, with Linux.Encoder.1, that Linux-specific ransomware gained traction. Despite the sophistication of ransomware in Windows systems, it is only in recent years that the capabilities have been directly transferred to Linux, as evidenced by a significant increase in attacks since 2020.
The CPR study reveals a trend toward simplification among ransomware families targeting Linux. Core functionality is often limited to simple encryption processes that rely heavily on external configurations and scripts, making them difficult to detect. The study also highlights specific strategies focused primarily on ESXi systems and identifies vulnerabilities in exposed services as primary entry vectors.
Linux ransomware is strategically tailored to medium and large companies
In terms of target and victim typology, Linux ransomware differs significantly from its Windows counterparts. While Windows is primarily used on personal computers and user workstations, Linux dominates certain server implementations. Linux ransomware primarily focuses on exposed servers or those within the internal network that are accessed through forks of Windows infections.
This targeting points to a clear trend: Linux ransomware is strategically tailored to medium and large enterprises, in contrast to the more general threats posed by Windows ransomware. The different internal structures of both systems also influence the attackers' approach to selecting folders and files for encryption. Linux-oriented examples often avoid critical directories to prevent damage to the system. This highlights the targeted and sophisticated nature of Linux ransomware compared to their Windows counterparts.
Comparing the encryption techniques of Windows and Linux systems, CPR finds a bias toward OpenSSL in Linux ransomware, with AES (Advanced Encryption Standard) as the common encryption cornerstone and RSA (Rivest–Shamir–Adleman) as the primary asymmetric choice. This consistency across different threat actors underscores the evolving cyber threat landscape.
More at CheckPoint.com
About check point Check Point Software Technologies GmbH (www.checkpoint.com/de) is a leading provider of cybersecurity solutions for public administrations and companies worldwide. The solutions protect customers from cyberattacks with an industry leading detection rate for malware, ransomware and other types of attacks. Check Point offers a multi-level security architecture that protects company information in cloud environments, networks and on mobile devices, as well as the most comprehensive and intuitive “one point of control” security management system. Check Point protects over 100.000 businesses of all sizes.