Wherever data needs to be protected, the Zero Trust principle is an indispensable security approach - especially in the healthcare sector. Cyber attacks are increasing rapidly there.
As healthcare organizations continue to go digital, one thing has become clear: the well-being of patients cannot come first if the digital systems that support them are compromised. According to the Journal of the American Medical Association (JAMA), the Frequency of cyber attacks on hospitals and healthcare systems to more than double between 2016 and 2021.
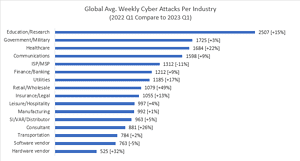
Research from Check Point Software Technologies confirms this trend, showing that the healthcare sector faced an average of 2023 attacks per week in the first quarter of 1.684 – a 22 percent increase compared to the previous year. This will make healthcare the third most targeted industry in 2023, ahead of finance, insurance and communications.
73 percent use old IT systems
These numbers are alarming, but explainable. The healthcare sector is a veritable goldmine of data, with much of it being managed by outdated IT systems that can easily be exploited. A survey by the Healthcare Information and Management Systems Society (HIMSS) found that 73 percent of healthcare organizations use legacy IT systems that are expensive to maintain and often have security vulnerabilities. The sector is therefore an easy – and potentially lucrative – target for ransomware operators. However, this vulnerability stems not only from software and systems, but also from the way data and devices are managed in each organization.
The zero trust principle
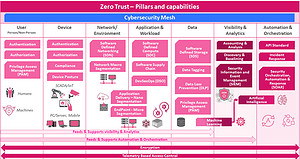
In sectors like healthcare, there is a division of responsibilities when it comes to cyber resilience. On one side is security enforcement, on the other side is network and policy control. This is best reflected in the "Seven Pillars of Zero Trust" as defined in the Forrester and National Institute of Standards and Technology (NIST) frameworks.
Zero Trust is a security model that works on the principle of "never trust, always verify". This means that access to resources and data should never be considered secure, even if it occurs within network perimeters.
The seven pillars of Zero Trust
The first five pillars are the users, the devices, the networks, the workloads, and the data. These pillars form the enforcement element of the framework, which enforces the principle of least privilege by requiring ongoing identity and verification checks. Visibility and analysis as well as automation and orchestration form the other two pillars. These pillars form the control and policy element of the framework and improve an organization's security posture through real-time monitoring and automated responses to security breaches.
By combining these pillars, organizations can create a trusted environment, and that's exactly what healthcare organizations should be doing to deal with the rising number of attacks.
Common network monitoring errors
There are some common mistakes that many healthcare organizations make when monitoring their network for threats.
Lack of a preventive concept
Just as it is better to vaccinate a patient to protect them from infection, it is better to detect and prevent cyberattacks before they reach a network. Real-time threat detection solutions can help identify abnormal traffic patterns, and real-time threat intelligence can actively block malware before it can enter a network.
Flat or non-segmented networks
Healthcare organizations continue to expand their networks as their services become more digitized. The vulnerable devices (endpoints) are no longer confined to a single location, but extend to homes and other offices. Therefore, it is important to segment the network through firewalls and device-level protection, or break it up into more manageable clusters. Just as a hospital can place fire doors around the building to prevent the spread of fire, a network should have barriers in place to prevent malware from spreading laterally.
No protection for end devices
An average 500 bed hospital can have up to 10.000 connected Internet of Things (IoT) devices to monitor, store and transmit patient information and other sensitive data. Enforcing a Zero Trust policy starts with “discovering” these devices on the network and then automatically applies a Low Privilege Zero Trust policy so that only relevant systems, or those that need access to perform their jobs, can access the devices.
Use of outdated security controls
To be effective, security controls must keep pace with the pace of innovation. Retrofitting these into existing applications means security is always a step behind innovation. To close this gap and continuously mitigate risk, security controls should be built into the application development process as early as possible.
Strengthen healthcare networks with Zero Trust
Implementing Zero Trust principles is essential for healthcare organizations to ensure the security of patient data and critical infrastructure. Network monitoring is a subset of Zero Trust visibility and analytics, and is essential to identifying and categorizing information and understanding data flow.
Workloads refer to any application or service running in private data centers or public clouds, and the principle of least privilege or "never trust, always verify" must be enforced here. Healthcare organizations can empower their application workloads with Zero Trust by implementing continuous identity verification and real-time preventive security measures. Zero Trust can be implemented in any application, on-premises or in the cloud, depending on the organization's security needs. For example, a centralized hospital has different needs than a nursing home or home care service, where staff are traveling with their devices or the devices are in different locations.
Never trust, always verify
Data also needs to be classified in order to be protected in the right way. Securing unstructured data such as text, photos, video and audio, and remote surgery with robotic systems such as "Da Vinci" all require different levels of protection and control.
The Pillars of Zero Trust can be leveraged and implemented in different ways to secure data pathways and automate threat response, but the underlying principle remains the same: never trust, always verify. If healthcare organizations are to survive the coming storm, they must adopt this cyberculture. Said Itai Greenberg, CSO, Check Point Software.
More at CheckPoint.com
About check point Check Point Software Technologies GmbH (www.checkpoint.com/de) is a leading provider of cybersecurity solutions for public administrations and companies worldwide. The solutions protect customers from cyberattacks with an industry leading detection rate for malware, ransomware and other types of attacks. Check Point offers a multi-level security architecture that protects company information in cloud environments, networks and on mobile devices, as well as the most comprehensive and intuitive “one point of control” security management system. Check Point protects over 100.000 businesses of all sizes.