Enterprises can now take full advantage of the benefits of a zero trust architecture while dramatically simplifying network design. New endpoint agents for macOS and Windows serve as a complete replacement for traditional virtual private networks.
Lookout has announced new Windows and macOS endpoint agents for its Lookout Secure Private Access Zero Trust Network Access (ZTNA) solution, facilitating the complete replacement of overburdened virtual private networks (VPNs) with cloud-based security. Enterprises can now take full advantage of the benefits of a zero trust architecture while dramatically simplifying network design. According to analysts at Gartner, by 2025, at least 70 percent of new remote access deployments will function primarily with ZTNA instead of VPN services. At the end of 2021 it was still less than 10 percent.
Too complex: ZTNA and VPN architectures at the same time
The initial ZTNA products offer limited traffic routing capabilities. Older VPN solutions, on the other hand, support a variety of protocols and complex use cases, making a complete VPN replacement difficult to implement in many enterprise environments. IT security teams are often forced to run ZTNA and VPN architectures simultaneously to support certain legacy applications such as VoIP phones. This limitation leads to complex network design that is costly to operate and maintain.
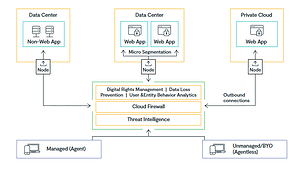
Lookout's new endpoint agents for Windows and macOS operating systems facilitate the full transition to a zero trust architecture with support for traffic control at both the network and application levels. When paired with Lookout Secure Private Access from the cloud, IT security teams can now completely replace the set of use cases supported by traditional VPNs and take full advantage of the benefits of a zero trust architecture.
VPN disrupts zero trust
The basic principle of Zero Trust is “never trust, always verify”. All users and devices are considered potential threats and must be constantly monitored and limited to the resources required to complete a specific task. VPNs, on the other hand, take an all-or-nothing approach to connectivity by allowing users to authenticate only once and then move freely around the network. This unrestricted access at the network level creates the conditions for lateral attacks. If a bad actor or malware can get past the VPN, they will have full access to all applications and sensitive data on the company's network.
Lookout's Secure Private Access, along with Windows and macOS endpoint agents, provides important security benefits. This includes:
- Unique insight into private application traffic: IT security teams can better understand how their users interact with private applications, from visibility to the actual data accessed.
- Advanced data security: The agents facilitate the deployment of advanced data security controls for enterprise private applications, including Data Loss Prevention (DLP) and Enterprise Digital Rights Management (EDRM) solutions.
- Granular traffic control to adapt to heterogeneous environments: The agents can be configured to route traffic to specific destinations based on factors such as user, device, and location. This ensures that only authorized users have access to sensitive data.
- Improved user experience with multi-tunnel traffic control: Agents route traffic to one of Lookout's many global Cloud Edge locations, providing the shortest path between the user and the business.
- Highly available, redundant multi-path routing: The agents use Lookkout's globally distributed Cloud Security Platform to provide end users with a highly available Security Service Edge (SSE) by leveraging advanced path selection and routing algorithms.
- Consistent Zero Trust Enforcement with Integrated Endpoint Security: Agents continuously monitor endpoint health when integrated with Endpoint Protection Platforms (EPPs), operating system security centers, and other endpoint security products.
About Lookout Lookout co-founders John Hering, Kevin Mahaffey, and James Burgess came together in 2007 with the goal of protecting people from the security and privacy risks posed by an increasingly connected world. Even before smartphones were in everyone's pocket, they realized that mobility would have a profound impact on the way we work and live.