Risk information enables protection for hybrid work models even after the pandemic. Trend Micro, one of the world's leading providers of cybersecurity solutions, provides insights into the security status of identities and devices based on comprehensive risk information. For customers, this is critical to achieving true zero trust security.
According to the analyst firm Forrester (1), “Zero Trust Network Access (ZTNA) is the security technology characteristic of the corona pandemic. While it (ZTNA) gently relieves users of outdated VPN technologies, it has led companies to rethink the use of security (and networks) both now and in the future. "
Verified devices are no longer secure either
Organizations can no longer assume that verified or trusted devices and individual identities are secure. On the one hand, this is due to a distributed workforce that uses a large number of systems to access company resources. On the other hand, these are hosted at different locations - from company data centers to cloud or SaaS applications.
Zero trust is a key strategy for increasing the security of critical data and systems. It is the right way to secure the constantly changing hybrid workplace in a more agile and effective way than conventional security architectures can do.
Understanding of risk based on zero trust solutions
However, there is great complexity in the market. Trust and access decisions are made without the appropriate context or a complete understanding of risk on the basis of so-called zero trust solutions.
"For years, vendors have claimed 'Zero Trust' by assigning this claim to all types of solutions without knowing how trust can actually be measured," says Richard Werner, Business Consultant at Trend Micro. “Trend Micro is ideally positioned to provide critical insights with its comprehensive Extended Detection and Response (XDR) solution. These include not only identity and device health, but email risk as well. Based on this, companies can build a successful zero trust strategy. "
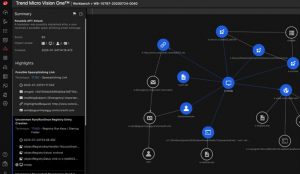
Basis: Trend Micro Vision One
Trend Micro's zero trust approach leverages the capabilities of Trend Micro Vision One to a large extent. The platform provides detailed insights thanks to a comprehensive XDR solution that covers email, cloud, networks and SaaS applications. Thanks to a continuous assessment of the security situation and comprehensive information, IT security teams can make well-founded decisions.
Benefits for companies
Risk and security status based on continuous evaluation of users, devices, apps and content. This supports automatic access control, flags incidents for investigation, and creates dashboards for CISOs and SOC teams to make informed decisions.
Every time a device or user tries to access corporate resources, a secure connection is established based on the health assessment. This includes a Cloud Access Security Broker (CASB) API integration for SaaS apps as well as policy enforcement points in front of company resources and supports the blocking of access to certain applications using existing endpoint agents.
Insight into email usage is particularly important for SOC teams, as phishing activity by internal users could indicate that user identities have been compromised - a common early sign of a ransomware attack.
Customers can use Trend Micro's risk assessments for Zero Trust to feed SASE and other third-party solutions via APIs for added value. Decision makers can use the insights and dashboard to better understand how their company's security posture is evolving over time.
More at Trendmicro.com
About Trend Micro As one of the world's leading providers of IT security, Trend Micro helps create a secure world for digital data exchange. With over 30 years of security expertise, global threat research, and constant innovation, Trend Micro offers protection for businesses, government agencies, and consumers. Thanks to our XGen™ security strategy, our solutions benefit from a cross-generational combination of defense techniques optimized for leading-edge environments. Networked threat information enables better and faster protection. Optimized for cloud workloads, endpoints, email, the IIoT and networks, our connected solutions provide centralized visibility across the entire enterprise for faster threat detection and response.