
Zero-day vulnerabilities are software vulnerabilities for which no patch exists to prevent exploitation of the vulnerability. According to the study, the Trend Micro Zero Day Initiative (ZDI) found 2021 percent verified security gaps in 64 - much more than providers such as Cisco, Google or Fortinet.
If the vulnerability is discovered by an attacker, this can have far-reaching consequences. The zero-day vulnerabilities "Hafnium" and "Log4Shell", which became known in 2021, were particularly drastic for many German companies. But even in the first half of 2022, there were already 18 zero-day vulnerabilities that were successfully exploited by cybercriminals - including the Microsoft Office vulnerability "Follina".
Over 1.600 vulnerabilities identified
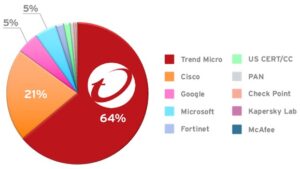
🔎 Trend Micro Zero Day Initiative (ZDI) dominates when it comes to finding vulnerabilities (Image: Trend Micro).
The independent study "Quantifying the Public Vulnerability Market: 2022 Edition" by the analyst firm Omdia examines all vulnerabilities disclosed by eleven different vendors. The Trend Micro Zero Day Initiative (ZDI) dominates the ranking in 2021 for the 15th year in a row with an initial detection of verified vulnerabilities of 64 percent, ahead of providers such as Cisco, Google and Fortinet. According to the study, there were over 1.600 vulnerabilities.
Although the number of reported vulnerabilities has increased, the more vulnerabilities that are discovered and published, the lower the chance for attackers to develop surprising zero-day attacks. The results show that the most effective way to detect vulnerabilities is to use attack detection software.
More at TrendMicro.com
About Trend Micro As one of the world's leading providers of IT security, Trend Micro helps create a secure world for digital data exchange. With over 30 years of security expertise, global threat research, and constant innovation, Trend Micro offers protection for businesses, government agencies, and consumers. Thanks to our XGen™ security strategy, our solutions benefit from a cross-generational combination of defense techniques optimized for leading-edge environments. Networked threat information enables better and faster protection. Optimized for cloud workloads, endpoints, email, the IIoT and networks, our connected solutions provide centralized visibility across the entire enterprise for faster threat detection and response.
