
In the latest report, security experts discover new attack vectors, cybercriminal resilience and familiar faces: The ESET Threat Report H1 2023 shows that the rules of the game for cybercriminals are changing. A special attack vector: OneNote instead of Office macros.
Office macros have been one of the top cyber threats for many years. After Microsoft changed the rules for this, OneNote attachments took over as malware launchers. This is a result of the latest edition of the ESET Threat Report H1 2023. In addition, between December 2022 and May XNUMX, ESET researchers made other worrying discoveries: Cyber criminals are showing remarkable adaptability to achieve their target not only by exploiting vulnerabilities get. In addition, someone believed dead returns in a roundabout way and the cards are also being reshuffled with other old ransomware acquaintances.
OneNote instead of Office macros: attack vector is changing
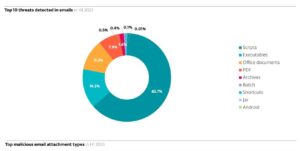
ESET Thread Report H1 2023: When it comes to dangerous email attachments, scripts are ahead with over 60 percent (Image: ESET).
“In the first half of the year, we have seen interesting developments from cybercriminals. They are becoming increasingly adaptable in terms of attack vectors: by exploiting vulnerabilities, unauthorized access, compromising sensitive data or defrauding private individuals. The search for new attack vectors also goes back to Microsoft's changed protection measures," explains Roman Kováč, Chief Research Officer of ESET. For security reasons, the tech giant announced in early 2022 that it would restrict VBA macros from the Internet in Office applications so that the scripts do not start automatically.
"As a result, we observed timely new attack attempts by cybercriminals to bypass Microsoft's security measures by replacing Office macros with OneNote files and using the option of embedding scripts and files directly in OneNote," Kováč continues. A dramatic increase can be seen from January to May 2023 in particular. According to ESET Telemetry, February and March were the busiest months, with OneNote files being used as a gateway for various malware families, including Emotet, RedLine Stealer, Qbot, and others. The subsequent adjustments to the default settings by Microsoft caused cybercriminals to look for alternative attack vectors, which is also reflected in the increasing number of brute force attacks on Microsoft SQL Server.
Deceptive Android credit apps and sextortion emails floating around
Due to rising interest rates, many people are looking for cheap loans: In the first half of the year, researchers observed an alarming growth in fake Android apps for financial assistance such as loans. These applications pose as legitimate personal loan brokers promising quick and easy access to money. However, the promised loan does not exist, this spyware only targets users' personal and financial information. Compared to the second half of 2022, detections of all money lending apps increased by almost 90 percent from January to May. This has increased the overall growth of Android spyware to 19 percent.
The comeback of so-called sextortion scams also shows that cybercriminals do not have to reinvent the wheel to make a profit. Extortion emails saw a whopping 201 percent increase in the first half of the year, mostly in Japan and several European countries.
Still active: Emotet, ransomware, crypto-malware
ESET telemetry data suggests that the operators of the once infamous Emotet botnet are struggling to find new attack vectors. In the first half of the year, there were three different malspam campaigns with slightly different infiltration and social engineering methods. The shrinking attacks and constantly changing approaches suggest that the results are not satisfactory and that another group may have taken over the botnet.
In the ransomware industry, hackers used previously leaked source code to create new variants of ransomware. “The leaked source code of ransomware families like Babyk, LockBit and Conti allows even laypersons to carry out ransomware activities. But for us as defenders, it allows us to cover and defend against a wider range of variants with a more general or known set of detections and rules,” says Roman Kováč, Chief Research Officer of ESET.
Cryptomining and cryptostealing capabilities are relocated
While cryptocurrency threats are on the decline, according to ESET telemetry — and not even revived by the recent surge in bitcoin's value — cryptocurrency-related cybercriminal activity remains active. Cryptomining and cryptostealing functions are increasingly being integrated into other malicious programs. This trend follows a pattern seen in the past, when, for example, a keylogger malware was recognized as a threat in its own right, but gradually evolved into a common capability of many malware families.
More at ESET.com
About ESET ESET is a European company with headquarters in Bratislava (Slovakia). ESET has been developing award-winning security software since 1987 that has already helped over 100 million users enjoy secure technology. The broad portfolio of security products covers all common platforms and offers companies and consumers worldwide the perfect balance between performance and proactive protection. The company has a global sales network in over 180 countries and branches in Jena, San Diego, Singapore and Buenos Aires. For more information, visit www.eset.de or follow us on LinkedIn, Facebook and Twitter.
