The European security manufacturer ESET has published its current "T1 2022 Threat Report". In it, the specialists summarize the most important statistics of the ESET detection systems and show notable examples from cybersecurity research.
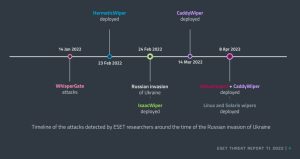
The latest edition of the ESET Threat Report reports on various cyberattacks related to the Russian invasion of Ukraine that were detected or repelled by ESET researchers. This also includes the comeback of the notorious malware Industroyer. This malware was intended to paralyze substations in the Ukraine.
Cyberwar in Ukraine is changing the threat landscape
ESET telemetry also recorded other changes in cyber threats that may be related to the situation in Ukraine. Roman Kováč, Chief Research Officer at ESET, explains why this report focuses on war-related cyber threats: “There are multiple conflicts raging in different parts of the world, but for us this one is different. Right on the eastern border of Slovakia, where ESET has its headquarters and several offices, Ukrainians are fighting for their lives and sovereignty.”
Criminals adapt
For the first time in more than two years, attempted attacks on RDP connections fell by almost half. But even with this regression, almost 60 percent of the RDP attacks recorded in the first quarter of 2022 came from Russia. Attacks on databases (SQL injections) also fell by 64 percent and on SMB protocols by more than a quarter. The ESET researchers see possible reasons for the decline in the abolition of remote work in companies after the end of many corona restrictions and in improved IT security measures.
Ransomware and scam campaigns are gaining momentum
Before the invasion, Russia was not on the target list of ransomware attacks. Since the invasion of Ukraine, it has been the most attacked country. In the first quarter, ESET researchers detected the most ransomware attacks in Russia at 12 percent, including lockscreen variants with the Ukrainian national greeting.
The number of amateurish ransomware and wiper software has also increased during this period. Their perpetrators often show their political views and turn the attacks into a personal vendetta. This trend is expected to continue or even intensify in the coming months. Fraudsters are also taking advantage of the war in Ukraine, and phishing and fraud campaigns are increasing. Immediately after February 24, calls for alleged charities and fictitious fundraisers to support Ukrainians began to appear.
Emotet returns
ESET telemetry also detected many other threats unrelated to the Ukraine war. "Emotet, the notorious and already thought dead malware that was mainly distributed via spam emails, has resurfaced and shot through the roof in our detection systems," explains Kováč. In March and April 2022, Emotet operators launched massive spam campaigns using Microsoft Word documents and the number of malware detections increased more than XNUMX-fold. However, according to Microsoft, this could soon be over, since the tech giant has disabled the macros attacked by the hackers in Office programs by default.
Trends in the ESET Threat Report
The new threat report provides an overview of the most important research results relating to further security gaps and malware developments. Examples include exploiting kernel driver vulnerabilities, highly dangerous UEFI vulnerabilities, cryptocurrency malware targeting Android and iOS devices, an unassigned campaign using DazzleSpy macOS malware, and Mustang's campaigns Panda, Donot Team, Winnti Group and the TA410 APT Group.
The Threat Report also includes an overview of various presentations by ESET researchers during the first quarter of the year. In addition, he provides an outlook on the contributions to the RSA and REcon conferences in June 2022, where the researchers will present insights into the discoveries of Wslink and ESPecter. The ESET research team will also publish further results at the Virus Bulletin Conference in September 2022.
More at ESET.com
About ESET ESET is a European company with headquarters in Bratislava (Slovakia). ESET has been developing award-winning security software since 1987 that has already helped over 100 million users enjoy secure technology. The broad portfolio of security products covers all common platforms and offers companies and consumers worldwide the perfect balance between performance and proactive protection. The company has a global sales network in over 180 countries and branches in Jena, San Diego, Singapore and Buenos Aires. For more information, visit www.eset.de or follow us on LinkedIn, Facebook and Twitter.