
Big or small, security flaws crop up in almost every company and organization that calls on the Sophos Rapid Response Team for help. The experts have summarized and evaluated the ten most common false arguments on the front lines against cyberattacks in the past year.
“We're much too small! Our endpoint protection also keeps attackers away from the server! Our backups are safe from ransomware! ”- The Sophos Rapid Response Team repeatedly encounters misjudgments in its fight against cyberattacks. Here is the list with the top 10.
Misconception 1: We are much too small as victims
Many victims of cyberattacks consider themselves too small, too uninteresting or not very lucrative to be threatened. Criminals take little care of this. Any person or micro business with a digital presence and use of computers is a potential victim. Most hacker attacks are still rarely carried out in the spectacular James Bond style with national state integration, etc., but are carried out by opportunists in search of easy prey. The most popular targets include companies with unpatched vulnerabilities or misconfigurations.
Anyone who thinks they are too insignificant as a target should still search their network for suspicious activities - such as the presence of Mimikatz (an open source application that allows the user to view and save authentication data) on the domain controller, to spot early signs of a possible attack.
Misconception 2: Endpoint protection is enough for us
Really? The attitude that endpoint protection is sufficient to stop threats and that servers do not need their own security measures is often exploited by attackers: Every error in configuration, patching or security makes servers a target of the highest priority for hackers.
The list of attack techniques used to attempt to evade or disable endpoint software and avoid detection by IT security teams grows by the day. Examples include human-powered attacks that exploit social engineering and many other vulnerabilities to gain access. On board: obfuscated malicious code that is injected directly into memory, “fileless” malware attacks, DLL (dynamic link library) loading, and attacks that use legitimate remote access agents such as Cobalt Strike in addition to everyday IT admin tools and techniques use. Traditional antivirus technologies struggle to detect and block such activity.
Intruders at the endpoint can hardly be stopped
Likewise, the assumption that protected endpoints can prevent intruders from making their way to unprotected servers is a misconception. According to the incidents investigated by the Sophos Rapid Response Team, servers are now the number one target and attackers can easily find a direct route to these "crown jewels" with stolen credentials. Unsurprisingly, most attackers are also familiar with a Linux computer, so these are just as much in focus. In fact, attackers often hack into Linux computers and install back doors there in order to use them as a safe haven and to maintain access to the targeted network. If a company relies only on basic security, without advanced and integrated tools such as behavioral and AI-based detection plus possibly a XNUMX/XNUMX human-run security operations center, then it is only a matter of time before intruders occur march past these defensive measures.
Misconception 3: We have robust security policies
It is important to have security policies for both applications and users. However, it is essential that these also correspond to the current IT infrastructure and are not completely out of date; they must be constantly checked and updated when new features and functions are added to the devices connected to the network. Techniques such as pen tests, tabletop exercises and test runs of the disaster recovery plans help here.
Misconception 4: Protected Remote Desktop Protocol (RDP) servers
They can be protected from attackers by changing the ports and introducing multi-factor authentication (MFA). Not quite. The standard port for RDP services is 3389, so most attackers will scan this port. However, when scanning for vulnerabilities, all open services are identified, regardless of which port they are on. Changing ports alone offers little or no protection.
In addition, while implementing multi-factor authentication is important, it will not add security if the policy is not enforced for all employees and devices. RDP activities should take place within the protective confines of a virtual private network (VPN), but even that cannot completely protect an organization if the attackers are already established in a network. Ideally, IT security should restrict or disable the use of RDP internally and as much as possible, unless its use is essential.
Misconception 5: Blocking IP addresses from high-risk regions
Blocking IP addresses from certain regions like Russia, China and North Korea protects us from attacks from those regions. Blocking is unlikely to do any harm, but it could create a false sense of security if businesses only rely on it. Attackers host their malicious infrastructure in many countries, e.g. with hubs in the USA, the Netherlands or other European countries.
Misconception 6: Backups protect us from the effects of ransomware
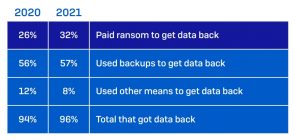
Study: State of Ransomware 2021 - a third of the companies certainly did not pay a ransom voluntarily (Image: Sophos).
Data backups are crucial in the event of data loss, a technical malfunction or a cyber attack. However, when these backup systems are connected to the network, they are within the reach of attackers and are prone to being encrypted, deleted or deactivated in the event of a ransomware attack. It should also be borne in mind that limiting the number of people with access to the backups does not significantly increase security, as the attackers have probably already spied on them in the network with access data. Furthermore, caution is advised when storing backups in the cloud - in one case investigated by the Sophos Rapid Response team, the attackers sent the cloud service provider an email from a hacked IT administrator account and asked him to stop all Delete backups. The provider complied with the request.
The industry standard for secure backups to restore data and systems after a ransomware attack is 3-2-1: three copies using two different systems, one of which is also offline. An additional note: offline backups do not protect the data from ransomware attacks, in which the criminals steal the data and threaten to publish it instead of 'just' encrypting it.
Misconception 7: Our employees understand security
According to the study "State of Ransomware 2021” 22 percent of companies believe they will be victims of ransomware in the next XNUMX months because it is difficult to stop end users from compromising security.
Social engineering tactics like phishing emails are becoming increasingly difficult to spot. The messages are often hand-written, precisely written, persuasive, and carefully selected. Employees need to know exactly how to spot suspicious messages and what to do if they receive one. Who do they notify so other employees can be put on alert?
Myth 8: Incident Response Teams Can Recover My Data After A Ransomware Attack
Unfortunately that is very unlikely. Attackers make far fewer mistakes today and the encryption process has improved. It is reckless to rely on the security specialists to find a way to reverse the damage. Automatic backups are also affected by most modern ransomware and it is hardly possible to restore the original data.
Myth 9: Paying the ransom will restore our data after a ransomware attack
This fallacy is arguably the most bitter, as according to the 2021 State of Ransomware survey, a company that pays the ransom recovers, on average, only about two-thirds (65 percent) of its data. Only 8 percent got all their data back, and 29 percent were able to recover less than half. Paying the ransom, while it seems the easiest option and might be covered by the cyber insurance policy, is not a solution to get back on your feet.
Also, data recovery is only part of the recovery process - in most cases, ransomware completely shuts down computers, requiring software and systems to be rebuilt from the ground up before data can be recovered. The State of Ransomware survey found that the recovery costs are, on average, XNUMX times the ransom demand.
Misconception 10: Ransomware is the complete attack - if we survive we are safe
The last bad news: this is unfortunately rarely the case. In the vast majority of cases, ransomware is just the point at which the attacker makes the victim aware that they are there and what they have done.
The attackers were likely to have been on the network days, if not weeks, before they launched the ransomware. They explored it, disabled or deleted backups, found the computers with important information or applications that they wanted to encrypt, removed information and installed additional user data or backdoors. Remaining in the victim's networks enables the attacker to launch a second attack. Whenever you want.
More at Sophos.com
About Sophos More than 100 million users in 150 countries trust Sophos. We offer the best protection against complex IT threats and data loss. Our comprehensive security solutions are easy to deploy, use and manage. They offer the lowest total cost of ownership in the industry. Sophos offers award-winning encryption solutions, security solutions for endpoints, networks, mobile devices, email and the web. In addition, there is support from SophosLabs, our worldwide network of our own analysis centers. The Sophos headquarters are in Boston, USA and Oxford, UK.
