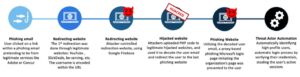
Zero Trust principles: More security in the cloud
Access to corporate networks is traditionally based on trust. This method is anything but secure. Security experts advise introducing a security infrastructure based on the Zero Trust principles. Companies are quite open about distributing permissions and access to their corporate networks to all employees. But now that more and more organizations are moving their applications and workloads from on-premises data centers to the cloud, the potential for unauthorized access, such as hackers, is growing. In the context of network modernization, the time is ripe for a security infrastructure based on the zero trust principle, believes NTT Ltd. and advises the following steps for implementation: 1….