
The new Sophos study "State of Ransomware 2022" shows: 67 percent of German companies have already been affected by ransomware. In 2020 it was still 46 percent. The average ransom paid in Germany almost doubled to over 250.000 euros.
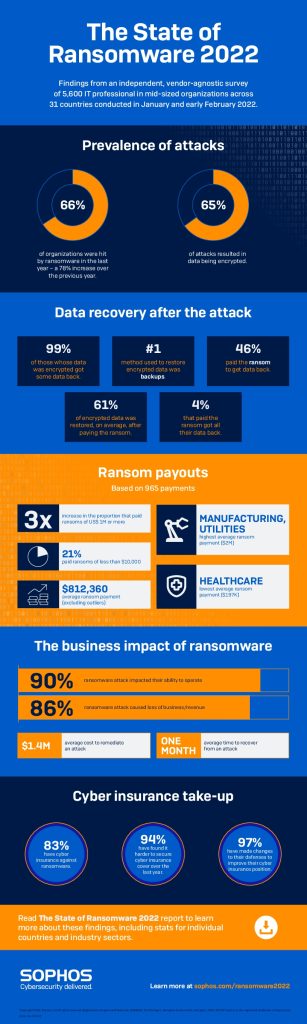
Sophos released its annual State of Ransomware 2022 study, which provides an overview of ransomware development in practice. The report shows that 67% of companies surveyed in Germany (66% globally) were affected by ransomware in 2021, up from 46% in 2020. The average ransom paid by German companies whose data was compromised at their largest ransomware attack has almost doubled to EUR 253.160. After no companies from Germany paid a ransom of EUR 925.789 (US$ 1 million) or more in the survey last year, this figure jumped to 9% in the most recent survey (11% globally).
42% (46% globally) of German companies whose data was encrypted paid the ransom to get their data back, even if they had other means of data recovery, e.g. B. Backups.
42% of German companies paid a ransom
"In addition to the escalating payments, the survey also shows that the proportion of victims willing to pay continues to rise, even when they have other options available," said Chester Wisniewski, principal research scientist at Sophos. “There can be several reasons for this, such as incomplete backups or preventing the publication of stolen data on a public leaks site. After a ransomware attack, there is often a lot of pressure to get back up and running as quickly as possible. Restoring encrypted data from backups can be a difficult and time-consuming process. Therefore, it seems tempting to pay a ransom for data decryption because it appears as a quick option. However, this approach is associated with high risks. Companies don't know what the attackers may have done on the network besides the ransomware attack, such as installing backdoors for future attacks or copying passwords. In the worst case, if organizations don't thoroughly sanitize the recovered data, they still end up with potentially malicious programs on their network and may be vulnerable to another attack."
Key findings from the 'State of Ransomware 2022' study
- Higher ransom payments: In 2021, 9% (11% globally) of German companies reported paying ransoms of EUR 925.789 (US$1 million) or more. In 2020, no German company paid more than EUR 925.789 in ransom (3% globally). The proportion of German companies that paid less than EUR 9.257 (US$ 10.000) has fallen to 35% from 2020% in 13.
- More victims pay ransom: In 2021, 42% (46% globally) of German companies whose data was encrypted by a ransomware attack paid the ransom. From a global perspective, 26% of companies that were able to recover encrypted data from backups in 2021 also paid the ransom.
- The impact of a ransomware attack can be immense: The average cost of recovering from a ransomware attack in 2021 for German companies was EUR 1.601.615 (US$ 1,4 million / EUR 1.296.105 globally). It took an average of one month to repair the damage and business disruption. 92% (90% globally) of German companies reported that the attack impacted their ability to operate and 84% of victims reported that they suffered business and/or lost revenue as a result of the attack.
- Many companies rely on cyber insurance to recover from a ransomware attack: In Germany, 80% (83% globally) of the companies surveyed had cyber insurance that covers them in the event of a ransomware attack. In 98% of German incidents, the insurer paid some or all of the costs incurred, with only 41% covering the entire ransom demand.
- Ninety-four percent of those who have purchased cyber insurance say their experience of purchasing cyber insurance has changed over the past XNUMX months: this perception is primarily reflected in increased cyber security requirements, more complex or expensive policies, and fewer Companies that offer insurance coverage.
Ransomware peak?
“The results suggest that we may have reached a peak in ransomware evolution, where attackers' greed for ever-increasing ransom payments collides head-on with a hardening of the cyber insurance market. Insurers are increasingly trying to reduce their ransomware risk and exposure,” says Wisniewski. “In recent years, it has become increasingly easy for cybercriminals to deploy ransomware as almost everything is available as a service. Also, many cyber insurance providers have covered a wide range of recovery costs due to ransomware, including the ransom, which has likely contributed to ever-increasing ransom demands. The results also suggest that cyber insurance policies are becoming tougher and ransomware victims may be less willing or less able to pay extremely large ransoms in the future. Unfortunately, this is unlikely to reduce the overall risk of a ransomware attack. Ransomware attacks are not as resource-intensive as other, more sophisticated cyberattacks. Therefore, every ransom is a lucrative reward and cybercriminals will continue to seek out easy targets.”
Best practices to protect against ransomware and similar cyberattacks
- Installation and maintenance of high-quality protective measures throughout the company. Regular checks and security checks ensure that the security precautions always meet the company's requirements.
- Active threat hunting to identify and stop attackers before they can launch their attacks. If the IT or security team does not have the resources or knowledge to do this themselves, managed detection and response (MDR) specialists should be engaged.
- Hardening of the IT environment by detecting and closing dangerous security gaps, such as unpatched devices, unprotected computers, or open RDP ports, are identified and eliminated by Extended Detection and Response (XDR) solutions.
- Be prepared for the worst. Organizations should know what to do when a cyber incident occurs and keep the contingency plan up to date.
- Creating backups and testing recovery so the business can get back up and running as quickly as possible and with minimal disruption.
About the Study
The State of Ransomware 2022 study looks at ransomware incidents and experiences in 2021. The survey was conducted by Vanson Bourne, an independent market research specialist, in January and February 2022. 5.600 IT decision makers were surveyed in 31 countries, in the USA, Canada, Brazil, Chile, Colombia, Mexico, Austria, France, Germany, Hungary, Great Britain, Italy, the Netherlands, Belgium, Spain, Sweden, Switzerland, Poland, Czech Republic, Turkey, Israel, United Arab Emirates, Saudi Arabia, India, Nigeria, South Africa, Australia, Japan, Singapore, Malaysia and Philippines. All respondents came from medium-sized companies with 100 to 5.000 employees.
Note: For the global survey, “ransomware affected” was defined as one or more devices affected by a ransomware attack, but not necessarily encrypted. Unless otherwise noted, respondents were asked to report their most important attack.
More at Sophos.com
About Sophos More than 100 million users in 150 countries trust Sophos. We offer the best protection against complex IT threats and data loss. Our comprehensive security solutions are easy to deploy, use and manage. They offer the lowest total cost of ownership in the industry. Sophos offers award-winning encryption solutions, security solutions for endpoints, networks, mobile devices, email and the web. In addition, there is support from SophosLabs, our worldwide network of our own analysis centers. The Sophos headquarters are in Boston, USA and Oxford, UK.
