Report: Attacks Exacerbate the Global Cybersecurity Crisis
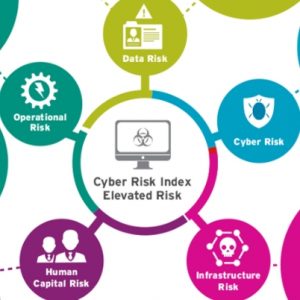
Further attacks exacerbate the global cybersecurity crisis, according to the latest NETSCOUT Threat Intelligence Report. Around 2021 million DDoS attacks were recorded from January to June 5,4. That is an increase of 11% compared to the same period last year. This development could break the record from 2020, with far-reaching effects on critical Internet gateways. NETSCOUT SYSTEMS, Inc. has published results in its semi-annual Threat Intelligence Report that underscore the dramatic impact of ongoing cyberattacks on businesses, public institutions and governments around the world. In the first half of 2021, around 5,4 million DDoS attacks (Distributed Denial of ...