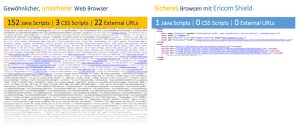
Safe surfing using the zero trust approach for websites, email links and downloads. Ericom Shield blocks cyber attacks via the web browser, protects users from phishing attacks, malware, ransomware and other threats from remote use. Shield allows completely transparent internet usage.
Most companies and institutions use different solutions to prevent employees from visiting problematic websites. The only problem is that between 10.000 and 30.000 new websites containing malicious code are identified every day. A single wrong click is enough to put the entire organization in danger: computers encrypted by malware, ransom demands, the loss of customer data and more can result. The conventional approach relies on antivirus software and firewalls to detect and block threats.
What is Remote Browser Isolation?
Remote Browser Isolation (RBI) is based on the basic concept of virtual browsers, but goes one step further. In contrast to RDS / VDI scenarios, all browsing activities are carried out in a remote location isolated from the local network. The remote, virtual browser runs within a dedicated Linux container, with each browser tab being assigned its own container. As soon as the user starts his first session by clicking on a link or entering a URL, one of the containers within the pool is assigned to this session. The system translates all active web content into pure image and audio files, which are streamed in real time to the end device of the user in order to enable fully transparent and interactive surfing on the Internet.
Since no web code is executed on the user's device, both the network and all endpoints are protected from malware, cyberattacks and other threats that may lurk in the original code of the pages visited. If the user closes or hides a browser tab, the corresponding container is immediately discarded, along with any potential malware that might have infected the company.
Advantages of RBI
Compared to classic virtual browsers, Remote Browser Isolation scores with a better user experience, lower technical overhead and greater security.
Technical consideration
Many virtual browsers run on RDS / VDI platforms, which means that hardware requirements and server / client configuration are not exactly trivial and may require the purchase of Microsoft CALs (Client Access Licenses). A Linux-based RBI container architecture places much lower demands on the hardware, which leads to noticeable cost reductions in the long term and makes the solution more scalable.
User experience - speed
Starting a virtual browser takes time, if only because it takes time for the RDP session to be established. Containerized remote browsers, however, start immediately.
Business security
The isolated containers in the RBI solution provide a new, pristine environment for every tab and session, which is thrown away as soon as the tab or session is no longer in use. This prevents malware (e.g. XSS) from becoming lodged and spreading in the company.
More at Giritech.de
About Giritech
Giritech supports companies, educational organizations, healthcare facilities and public clients in the implementation of a consistent enterprise mobility and security strategy. As a long-standing distributor for manufacturers such as Soliton Systems, Ericom Software, WiseMo and Faronics Corp., Giritech has the necessary experience in on-site and remote implementation, provides pre- and after-sales support and supports users in choosing the right products for specific environments.