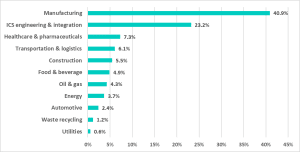
Kaspersky experts have discovered a new, rapidly evolving series of spyware campaigns targeting over 2.000 industrial companies worldwide, stating: short-lived attack scenarios are increasing, data is being offered for sale on marketplaces, an estimated 7.000 compromised or stolen corporate accounts.
Unlike many traditional spyware attacks, these attacks have a limited number of targets and a very short lifespan for each malicious program. The captured data was offered for sale on more than 25 marketplaces.
Company data on 25 marketplaces for sale
In the first half of 2021, Kaspersky ICS CERT experts noticed an unusual anomaly in the statistics of spyware threats blocked on ICS computers. Although the malware used in these attacks belongs to well-known spyware families such as Agent Tesla/Origin Logger, HawkEye and others [2], these attacks stand out from the mainstream because the number of targets in each attack is very limited (ranging from a handful to to a few dozen) and the lifespan of each malicious program is very short.
A more detailed analysis of 58.586 spyware samples blocked on ICS computers in the first half of 2021 showed that around 21,2 percent of them belonged to this new attack series with limited scope and short lifespan. Their life cycle is limited to around 25 days - significantly less than the lifespan of a "conventional" spyware campaign.
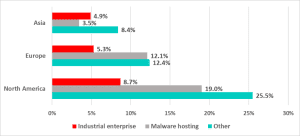
Although each of these "anomalous" spyware samples is short-lived and not widespread, they account for a disproportionate share of all spyware attacks. In Asia, for example, one in six computers attacked with spyware was affected (2,1 percent out of 11,9 percent), in Europe it was 0,7 percent out of 6,3 percent.
Phishing emails as an entry point into the company
Most of these campaigns are distributed from one industrial company to another via well-crafted phishing emails. Once the attacker has penetrated the victim's system, he uses the device as a C2 (Command and Control) server for the next attack. With access to the victim's mailing list, cybercriminals can misuse corporate email and further proliferate the spyware.
According to Kaspersky's ICS-CERT telemetry, over 2.000 industrial companies worldwide were embedded in the malicious infrastructure and abused by cybercriminals to carry out the attack on contact organizations and business partners. Kaspersky estimates the total number of corporate accounts compromised or stolen as a result of these attacks at over 7.000.
Brisk online trading with hijacked data
The captured sensitive data often ends up on different marketplaces. Kaspersky experts have identified more than 25 different ones selling the stolen credentials from these industrial campaigns. The analysis of these marketplaces revealed a high demand for access data for company accounts, especially for remote desktop accounts (RDP). Over 46 percent of all RDP accounts sold on the surveyed marketplaces belong to companies in the US, with the rest coming from Asia, Europe and Latin America. In Germany, this was almost 4 percent (almost 2.000 accounts) of all sold RDP accounts that affected industrial companies.
Spyware as a Service
Another growing market is Spyware-as-a-Service. Ever since the source codes of some popular spyware programs were released, they are easily available in the form of a service in online stores. Developers not only sell malware as a product, but also license a malware builder and access to infrastructure preconfigured to create the malware.
“In 2021, cybercriminals made extensive use of spyware to attack industrial computers. Today we are observing a new, rapidly evolving trend in the industrial threat landscape,” comments Kirill Kruglov, Security Expert at Kaspersky ICS CERT. “To avoid detection, cybercriminals reduce the size of each attack and limit the use of each malware sample, quickly replacing it with a newly created one. Other tactics include extensive abuse of corporate email infrastructure to spread malware. This is different from anything we've seen with spyware before. We expect such attacks to become more prevalent this year."
More at Kaspersky.com
About Kaspersky Kaspersky is an international cybersecurity company founded in 1997. Kaspersky's in-depth threat intelligence and security expertise serve as the basis for innovative security solutions and services to protect companies, critical infrastructures, governments and private users worldwide. The company's comprehensive security portfolio includes leading endpoint protection as well as a range of specialized security solutions and services to defend against complex and evolving cyber threats. Kaspersky technologies protect over 400 million users and 250.000 corporate customers. More information about Kaspersky can be found at www.kaspersky.com/
Kaspersky ICS Predictions: https://securelist.com/threats-to-ics-and-industrial-enterprises-in-2022/104957/