
Since January 2023, cybercriminals have been targeting implementations of Zoho Corporation's ManageEngine software solutions worldwide with an opportunistic attack. Cyber criminals use automated scans to tap into a large field of potential victims of ransomware or industrial espionage.
Bitdefender Labs analyzed the first attacks in their telemetry. The new campaign is another example of the more common opportunistic, initially automated vulnerability scans by cybercriminals followed by hybrid targeted attacks. The aim of the attackers is to execute code remotely (Remote Code Execution – RCE) in order to play additional payloads or to start industrial espionage. Around 2.000 to 4.000 servers with Internet access are potentially affected worldwide. A patch is strongly recommended. ManageEngine had already published the report about the vulnerability CVE-10-2023 on January 2022, 47966, which affects 24 products.
Vulnerability patch available
ManageEngine, the enterprise IT management division of Zoho Corporation, offers an extensive portfolio of real-time tools to monitor IT environments. Attacks on the ManageEngine exploit CVE-20-2023 have been increasing worldwide since January 2022, 47966. This Remote Code Execution (RCE) allows the complete takeover of the compromised systems by an unauthenticated attacker. A total of 24 different ManageEngine products are vulnerable. Two to four thousand internet-facing servers have ManageEngine versions that are potential victims with the Proof of Concept (PoC) documented by the Horizon3.ai team. Not all servers can be attacked with this PoC because the XML framework Security Assertion Markup Language (SAML) must be configured.
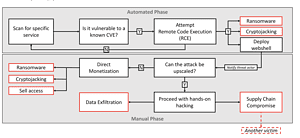
🔎 Hybrid attacks: The automated scan for the RCE vulnerability turns into a targeted attack (Image: Bitdefender).
Hybrid spray-and-pray attacks are trending
The current attacks are another example of a growing trend to launch scalable global attacks. The starting point is an automated opportunistic scan for an RCE vulnerability, often after a published PoC. Such attacks have already targeted Microsoft Exchange, Apache or VMware ESXI environments. The vulnerable systems discovered in the scan are then automatically compromised. As a result of such "spray-and-pray" tactics, even if many companies patch their systems, the cybercriminals can attack numerous other servers with Internet connectivity.
Unfolded risk potential
In unpatched systems, the attackers then implement additional tools. Initial access brokers selling their knowledge of vulnerabilities attempted to initialize AnyDesk software for persistent remote access. In other cases, the perpetrators played the payload of a new Buhti ransomware attack. Others tried to exploit the Cobalt Strike industrial espionage simulation tool or the RAT el Red teaming tool for pentesting and alienate them for their purposes.
The attackers often modify the PoC only minimally. As a result, the immediate effect of an attack is initially only small. Many victims therefore only react with temporary repairs or workarounds. The systems are then initially considered immune, but are open to the next modification by the attackers.
Companies should urgently patch their systems. Solutions that assess the reputation of IP addresses, domains or URLs are also important. Extended detection and response approaches also help. External help from managed detection and response services also improves the defense against such attackers.
More at Bitdefender.com
About Bitdefender Bitdefender is a leading global provider of cybersecurity solutions and antivirus software, protecting over 500 million systems in more than 150 countries. Since it was founded in 2001, the company's innovations have consistently ensured excellent security products and intelligent protection for devices, networks and cloud services for private customers and companies. As the supplier of choice, Bitdefender technology is found in 38 percent of security solutions deployed around the world and is trusted and recognized by industry experts, manufacturers and customers alike. www.bitdefender.de
