Chrome's bug bounty program is worth it: programmers and specialists have reported 7 highly dangerous vulnerabilities to Google and received a reward. Google also immediately provides the updates for users. Sole proprietorships and SMEs should be prepared to click one more time.
The latest Chrome update contains 7 updates for high-risk vulnerabilities. In companies, the admins ensure that Chrome remains up to date. Individual companies and SMEs should definitely click in the help area - the further update happens automatically. Work PCs often run through and as long as the browser is not closed and reopened, no update happens!
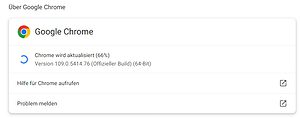
Trigger Chrome update
If the update is not triggered by a group policy, you should proceed as follows: Users only have to restart the browser for the update or, even easier, select Settings >Help >About Google Chrome. The information page for the browser then opens. If the update wasn't done yet, Chrome will now just do it automatically.
The current update brings Chrome for Windows to version 111.0.5563.111, Chrome for Mac and Linux to 111.0.5563.110. It will fix the following 7 security issues.
- High CVE-2023-1528: Use-After-Free (UAF) in passwords
- High CVE-2023-1529: Out of range memory access in WebHID
- High CVE-2023-1530: Use-After-Free (UAF) usage in PDF
- High CVE-2023-1531: Use-After-Free (UAF) usage in ANGLE
- High CVE-2023-1532: Out-of-bounds reading in GPU video
- High CVE-2023-1533: Use-After-Free (UAF) in WebProtect
- High CVE-2023-1534: Read out of bounds in ANGLE