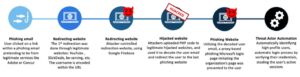
Cyber criminals are increasingly using multi-factor authentication (MFA) to hijack executive accounts. That's what IT security experts from Proofpoint found out. They saw an increase of over 100 percent over the past six months in incidents where cybercriminals were able to gain access to the cloud accounts of high-level executives at major companies.
More than 100 companies worldwide with a total of over 1,5 million employees are affected. The criminals used EvilProxy for their attacks. This is a phishing tool with a reverse proxy architecture that allows attackers to steal MFA-protected credentials and session cookies.
Attackers bypass MFA protection
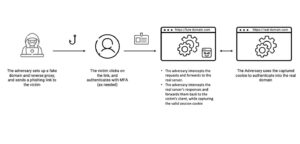
🔎 AitM Transparent Reverse Proxy: This is how attackers circumvent the MFA protection: the phishing link leads to a fake login page on which a user transmits the correct MFA code (Image: Proofpoint)
Proofpoint experts assess these new attacks: “Employee credentials are highly sought after by cybercriminals: they can provide access to valuable or sensitive company information and user accounts. While credentials generally offer a variety of attack vectors, not all credentials are equally valuable. Research shows that criminals often target specific functions or departments. In doing so, they have to constantly develop their methods and techniques, for example to overturn multi-factor authentication.
Contrary to popular belief, MFA is not a panacea against sophisticated cloud-based attacks. Once in, malicious actors can hide around an organization undetected and launch sophisticated attacks at will. Off-the-shelf MFA bypass phishing kits are now ubiquitous, allowing even non-technical criminals to launch a phishing campaign and trick employees into giving up their account credentials.”
Reverse Proxy Abuse
The growing use of MFA has led to the proliferation of phishing kits and tools that help bypass this layer of security. Cyber criminals are increasingly using Adversary-in-the-Middle (AitM) phishing kits like EvilProxy to steal credentials and session cookies in real-time.
EvilProxy's effectiveness as a phishing tool is well known. However, Proofpoint's experts identified a worrying gap in IT security leaders' awareness of the risks and potential consequences, such as Business Email Compromise (BEC) and Account Takeover (ATO).
Phase 1: Phishing with EvilProxy
Since early March, Proofpoint specialists have been monitoring a campaign that uses EvilProxy to attack thousands of Microsoft 365 user accounts. The total volume of this campaign is impressive: Between March and June 2023, approximately 120.000 phishing emails were sent to hundreds of target organizations around the world.
In the phishing phase of their attacks, the criminals used three main techniques:
- Brand impersonation: The senders impersonate trusted services and applications, e.g. B. Concur Solutions, DocuSign and Adobe.
- Scan blocking: The attackers used protection against cyber security scanning bots to make it difficult for security solutions to analyze their malicious websites.
- Multi-stage chain of infection: Attackers redirect traffic via openly accessible legitimate redirects.
To hide their emails from automatic scanning tools, the attackers use special email encoding and use legitimate websites that have been hacked to upload their PHP code and decrypt a specific user's email address .
Stage 2: Account Compromise
The list of targeted users includes many high-level targets, e.g. B. Managing Directors, Corporate Directors, C-Level Executives and VPs in leading companies. These individuals are particularly valued by criminals because they potentially have access to sensitive data and assets. Of the hundreds of compromised users, approximately 39 percent were senior management (“C-level”) employees, including 17 percent CFOs and 9 percent presidents and CEOs. Attackers also show interest in lower-level management, focusing their efforts on employees with access to assets or sensitive information.
Phase 3: Abuse after compromise
Once attackers gain access to a victim's account, they establish themselves in the victim's cloud environment. On multiple occasions, the attackers used a native Microsoft 365 application to perform MFA manipulations. Using “My Sign-Ins,” the attackers were able to add their own multi-factor authentication method, providing persistent access to compromised user accounts. They prefer the method via an authentication app with message and code.
More at Proofpoint.com
About Proofpoint Proofpoint, Inc. is a leading cybersecurity company. The focus for Proofpoint is the protection of employees. Because these mean the greatest capital for a company, but also the greatest risk. With an integrated suite of cloud-based cybersecurity solutions, Proofpoint helps organizations around the world stop targeted threats, protect their data, and educate enterprise IT users about the risks of cyberattacks.