The war in Ukraine is also a cyber war that promotes cyber espionage. Bitdefender Labs discover recent attacks on the Elephant framework. Attacks also take place through phishing with the download of supposed Bitdefender AV software. A summary of current cyber espionage.
Companies in the attacked country or in supporting nations connected to Ukraine are threatened by classic IT attack mechanisms, the perpetrators of which are politically motivated this time. In addition to deleting information, these include espionage. The Bitdefender Labs have analyzed the sophisticated attack mechanisms of the so-called Elephant Framework used for this.
Cyber war worsens global cyber security situation
Threat intelligence experts and analysts from managed detection and response teams have been monitoring the cybersecurity landscape since the outbreak of war. As expected, companies and organizations in Ukraine, especially in the areas of public authorities and critical infrastructure, are among the preferred victims. The pro-Russian UAC-2021 group has been actively engaged in cyber espionage since March 0056. The group – also known by the names Lorec53, UNC2589, EmberBear, LorecBear, BleedingBear, SaintBear and TA471 – is responsible for data exfiltration attacks using stealer malware such as OutSteel or GraphSteel. GraphSteel in particular uses a sophisticated set of techniques to find out passwords or information in the widely used Office formats such as .docx or .xlsx and other important data types such as .ssh, .crt, .key, .ovpn, or .json exfiltrate.
GraphSteel - Part of the Elephant framework
The complexity and professionalism of such attacks are demonstrated by attacks with GraphSteel, the authors of which are most likely from the environment of the UAC-0056 group. The GraphSteel malware is part of the Elephant framework, a malware toolset written in the Go programming language. Attackers recently used them in a series of phishing attacks against Ukrainian government agencies (gov.ua targets).
First, they started with a sophisticated spear phishing attack. The hackers showed high expertise in social engineering attacks and used spoofed Ukrainian email addresses. The contents of the fake emails were alleged official announcements or topics related to Corona. In an email, the alleged author warned of an increase in Russian cyber attacks, gave security tips and referred to an alleged download of Bitdefender software. The victims compromised their computers either by clicking on a link in the email text or by opening an Excel spreadsheet with embedded macros.
Launcher - dangerous Python script
In some cases, the hackers use a Python script that has been converted to an executable file as a launcher. In other cases, like the entire Elephant framework, they wrote the code in the Go programming language. Perhaps a factor in the decision was that not all security software detects malware written in Go. This in turn is probably due to the fact that programmers, both good and bad, do not use Go very often. Another advantage of the language for the hackers is that the payload can be compiled for both Windows and Linux without changing the code. It is also easy to use and can be extended with third-party malware modules. The launcher then acts as a combination downloader or dropper, connecting the victim system to the command and control server to announce its availability and receive an executable malware payload when the time comes.
Downloader - transports malware
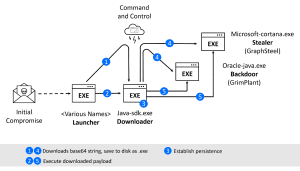
The downloader then loads two different malware files: GraphSteel (Microsoft-cortana.exe) and GrimPlant (Oracle-java.exe), both of which run automatically. GrimPlant allows to run PowerShell commands remotely. GraphSteel steals data such as access data, certificates, passwords or other sensitive information.
GraphSteel Stealer
The main purpose of GraphSteel is the exfiltration of files, which the malware then transmits encrypted with AES cipher over port 442. The tool uses web sockets and the GraphQL language to communicate with the command and control server. The stealer steals access data for Wifi, Chrome, Firefox as well as data from the password vaults, the Windows Credential Manager or SSH sessions and Thunderbird.
Supposedly on behalf of Bitdefender
🔎 Parallel attacks with two payloads after downloading malware disguised as Bitdefender AV software (Image: Bitdefender).
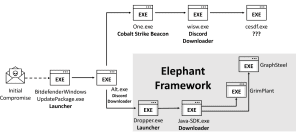
According to an entry from March 11, 2022 in the CERT-UA, other attacks from the UAC-0056 environment use urgent appeals to increase IT security and to download a supposed Bitdefender antivirus product from a supposed Bitdefender.fr site their attacks. But behind Bitdefender.fr is the domain forkscenter.fr with a spoofed Bitdefender.fr website.
This attack first installs a Discord downloader, which then implements two executable files: Alt.exe, a well-known Go launcher that downloads the Elephant Framework, and One.exe, a Cobalt Strike Beacon. In the end, in the latter case, a cesdf.exe is downloaded, which unfortunately is not available for analysis at the moment because the administrators of the attacked organization have meanwhile switched off their server.
Repelling such complex attacks requires tiered cyber security that can repel an attack during several phases: as early as blocking the phishing email, executing the payload or preventing further compromise and communicating with the C&C -Server.
More at Bitdefender.com
About Bitdefender Bitdefender is a leading global provider of cybersecurity solutions and antivirus software, protecting over 500 million systems in more than 150 countries. Since it was founded in 2001, the company's innovations have consistently ensured excellent security products and intelligent protection for devices, networks and cloud services for private customers and companies. As the supplier of choice, Bitdefender technology is found in 38 percent of security solutions deployed around the world and is trusted and recognized by industry experts, manufacturers and customers alike. www.bitdefender.de