
Manufacturer Progress Software has just released the 2nd update for MOVEit Transfer and MOVEit Transfer Cloud, so the company is now quickly adding a patch for a 3rd vulnerability. Just one day earlier, it was said that no further vulnerabilities were expected. Again it is a SQL injection vulnerability - a patch is essential!
The message is just now 2nd vulnerability here on B2B-Cyber-Security.de appeared, there is a message about the third vulnerability. Companies using MOVEit Transfer must patch the vulnerability. The appropriate patch is already available. Many users and administrators may already be confused as to which patch versions are the right ones. Progress Software provides guidance on which versions require which patch accordingly.
Admins can hardly keep up with patching
Progress Software said it worked with external cybersecurity experts to further review the existing code. The second vulnerability was found on June 09th, 2023. Since this is not closed by the first patch, companies urgently need to install the second patch - for MOVEit Transfer and MOVEit Cloud. The 2rd patch now probably refers to MOVEit Transfer again. The following gaps must be closed:
Patch 1: CVE-2023-34362 (May 31, 2023)
Patch 2: CVE-2023-35036 (June 9, 2023)
Patch 3: CVE-2023-35708 (June 15, 2023)
CLOP APT Group publishes first company names
Progress Software presents all dependencies and the history of the vulnerabilities online. Since the code is still being tested, it is possible that further patches will follow. Meanwhile, the CLOP APT group keeps updating their leaks page. There are more and more names of companies that are said to be affected. Only the companies can confirm whether this is really the case.
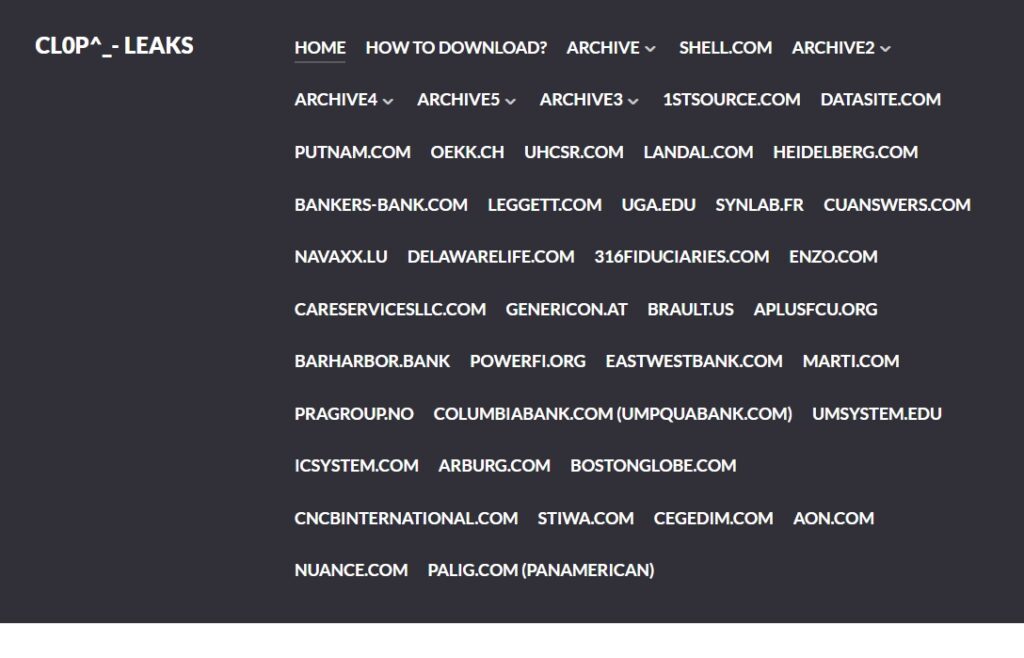
🔎 According to the CLOP Group, the listed companies lost data through the MOVEit Transfer vulnerability, but were unwilling to pay ransom. Whether this is true is unconfirmed. The companies themselves have not yet published any statements (Image: B2B-CS).
At the same time, the group announced that they had received many e-mails from the authorities because data had also been leaked there. CLOP would immediately delete this data as it is "solely financially motivated and doesn't care about politics". Meanwhile, cybersecurity companies like Tenable have reported that CLOP had also skimmed US government data.
More at Progress.com
