REvil has been one of the most prolific ransomware-as-a-service campaigns in recent memory. Thousands of technology companies, managed service providers, and organizations from a wide variety of industries worldwide have been among their victims. Bitdefender draws the preliminary balance sheet of an extortion enterprise.
The cooperation between security authorities and IT experts led to great success in the second half of 2021. Joint efforts were necessary because the cyber criminals also cooperated successfully. The experts at Bitdefender Labs take stock of the – perhaps only temporary – failure of a successful wave of ransomware-as-a-service.
International strikes against REvil backers
Most recently, international investigators struck heavy blows against the criminal REvil backers: In the course of a raid in November 2021, the US Department of Justice arrested so-called affiliates, i.e. partners or participants in the REvil network, and confiscated around six million US dollars in ransom money. Then, in January 2022, Russia's domestic intelligence agency FSB and Russian police arrested fourteen other suspected REvil members and seized additional multimillion-dollar financial assets.
Ransomware as a business model
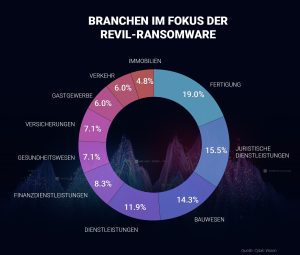
In the eyes of the Russian authorities, one of the most successful ransomware groups with annual sales of 100 million US dollars and a market share of 16,5 percent has been crushed. To achieve such a result, the RaaS operators attacked a wide variety of industries—most notably manufacturing, legal services, and construction (see Figure 1). The deal initially thrived and secured large profits for those involved: Bitdefender estimates that around ten core members and at peak times around 60 other partners took part in the actions. The latter received around 70 to 80 percent of the profits.
A mature company
REvil exemplarily shows the power and degree of organization of criminal ransomware-as-a-service models. In the affiliate network, developers, the attackers and those who carried out the penetration tests, as well as the ransom collectors worked closely together and also thought about the infrastructure to collect agreed amounts. They even set up support for victims who were willing to pay: they could pay the ransom via a portal. In addition, the criminal service employees advised the attacked organizations on acquiring cryptocurrencies or helped them use the TOR browser.
The criminal milieu also rewards competence
Quality distinguishes itself in the informal economy. This was evident in the REvil group: the better the malware code and the associated services became, the more professional partners joined the successful model. Further improvements brought even more rewarding targets within attacker's reach. The actors obtained higher ransoms, which they immediately reinvested in the RaaS: in new services or in new staff. The criminal associates were often sought-after professionals who moved from one affiliate partner to another.
Victim dialogue as customer communication
The cyber criminals addressed their victims like a customer. So they demanded the ransom according to a fixed pattern, only the keys and the URL differed. The ransom collectors also tried to inspire confidence in the victims. A personalized salutation ("Welcome ") belonged to the "good tone". From the beginning of 2020, the attackers then gave a supposed guarantee that their own REvil decryptor would work better than that of another criminal organization. It promised a recovery rate of nearly 100% compared to just 87%.
Staged Threats
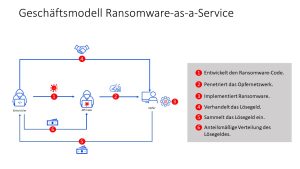
Joint work - joint profit - institutionalized operation: The ransomware-as-a-service model (Image: Bitdefender).
On the other hand, the RaaS partners built a multi-layered threat potential in which encryption was just one part of several. With reference to the European General Data Protection Regulation, they not only threatened to encrypt data, but also to disclose it. Which would have resulted in an obligation to report, damage to your image that should not be underestimated and, in the worst case, a fine. If the ransom was not paid, the criminals systematically increased the pressure, published leaked data and then demanded a ransom to stop this process. The third level of escalation was distributed denial of service attacks on the victims and their business partners.
The REvil collapse
In addition to the pursuit pressure and the availability of decryptors also developed by Bitdefender, internal factors also contributed to slowing down the success of REvil from autumn 2021. A work-sharing process like RaaS is based on the reputation and mutual trust of those involved. Apparently, the REvil initiators lost the necessary reputation within the cyber-criminal community. On the one hand, this was due to their provocative and loud demeanor, which violated a code of conduct in the cyber criminal underground. On the other hand, the attack on the healthcare industry or on pharmaceutical manufacturers and drug researchers during the pandemic was not without controversy among the criminal semi-public. Criminals of the old school found this counterproductive and hoped that these companies would quickly develop an antidote - because then the economy would get going again faster and higher ransoms could be demanded again.
Common and international defense works
The REvil complex has shown that only a common answer helps against a group of cyber criminals: on the technological side, a combination of technologies and services such as managed detection and response (MDR), heuristic analysis and machine learning on the one hand, as well as knowledge and expertise and intuition of the IT security experts on the other hand. Tools like decryptors also contributed. With the decryption tool released by Bitdefender in autumn 2021, 1.400 companies were able to decrypt files with a total value of half a billion US dollars themselves. On the personnel side, close cooperation between state and private sector actors in IT security is important. And that worldwide, because cybercrime knows no national borders.
More at Bitdefender.com
About Bitdefender Bitdefender is a leading global provider of cybersecurity solutions and antivirus software, protecting over 500 million systems in more than 150 countries. Since it was founded in 2001, the company's innovations have consistently ensured excellent security products and intelligent protection for devices, networks and cloud services for private customers and companies. As the supplier of choice, Bitdefender technology is found in 38 percent of security solutions deployed around the world and is trusted and recognized by industry experts, manufacturers and customers alike. www.bitdefender.de