A ransomware attack is enough for most companies as a limit. But two at once is an apocalypse scenario, albeit quite exciting for security professionals. Sophos took a closer look at the rare case, which is also a clash of modern and traditional ransomware tactics.
Sophos releases its research into a dual ransomware attack in which a ransom note from Karma ransomware operators was encrypted 24 hours later by the Conti Group. Conti, another ransomware community, was operating on the infected network at the same time.
Karma group meets Conti group in the same network
The Sophos analysts describe the dual attack in detail in their report and explain how both actors gained access to the network via an unpatched Microsoft Exchange Server. After that, however, they used different tactics to launch their attacks.
Sean Gallagher, Senior Threat Researcher at Sophos, explains how Karma and Conti behaved: “Becoming the victim of a dual ransomware attack is a nightmare scenario for any organization. In total, a period of four days can be identified in which Conti and Karma attackers acted simultaneously in the targeted network: they moved around each other, made downloads, executed scripts, installed Cobalt Strike and collected and exfiltrated data.
Conti Group Suppresses Karma Blackmail
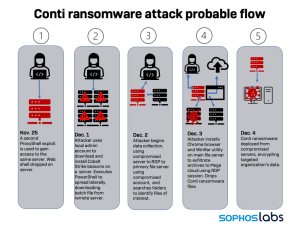
The Karma actors rolled out the final phase of their attack first, leaving a ransom note on computers demanding Bitcoin payment. As compensation, the stolen data would not be published. Then Conti struck, encrypting the targeted files using a more traditional ransomware method — ironically including the Karma ransom note.
Recently, we've been seeing more and more cases where hacker groups using the same ransomware for their attacks teamed up and used ProxyShell exploits to infiltrate the target network. There are also examples of different actors exploiting the same vulnerability to gain access to their victim. The current case, in which two completely unrelated ransomware groups attacked a target at the same time, shows how crowded and competitive the ransomware landscape has become.”
The dual attack - a time sequence
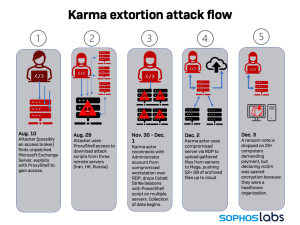
- August 10, 2021
The Sophos analysts assume that the attack was launched on this day. The criminals, possibly initiated by access brokers who act as a kind of broker in the cybercrime ecosystem and sell stolen access to systems, use a ProxyShell vulnerability to gain access to the network and secure a base on the compromised server.
- 30 November 2021
The investigation reveals that almost four months passed before Karma surfaced on November 30, 2021 and exfiltrated more than 52GB of data to the cloud.
- 3 December 2021
Three activities will take place on this date:
The Karma attackers leave a ransom note on 20 computers demanding a ransom or they would not be able to decrypt the data.
Meanwhile, Conti operated quietly in the background and exfiltrated information.
The victim brought the Sophos Incident Response Team on board for help against the karma attack.
- 4 December 2021
Conti rolls out its ransomware. In the forensic investigations, the Sophos team tracked the start of the Conti attack on another ProxyShell vulnerability, which was deployed on November 25, 2021.
Combination of technology as protection
Gallagher recommends the combination of technology and human expertise to protect against such attacks: "Whether the initial access broker sold access to two different ransomware groups or whether the vulnerable Exchange Server was just an unfortunate target for multiple ransomware attackers remains to be seen uncertain. The fact is that a double ransomware attack was possible. This is a powerful argument for patching known vulnerabilities immediately and relying on a communicating IT security system that can identify and block attackers at every stage of their attack chain. In a further step, the proactive, human-led threat search can investigate any suspicious behavior in detail. This includes things like unexpected remote logins or using legitimate tools outside of their normal pattern – all of these situations can be early signs of an imminent ransomware attack.”
Security companies are also being attacked
Last week, a Ukrainian security researcher released several years of chat logs and files from the Conti group. These logs mention how the Conti group also attempted to license Sophos Intercept X, and failed. According to the chat, they did this to test their latest malware and see if it would be detected by Sophos products. This is a common practice of cybercriminals and therefore various preventive measures are active at Sophos.
The chat logs show that Conti's attempts to bypass Sophos products were unsuccessful and that they then activated a trial to purchase a license as a next step. Conti's goal was to study the Sophos solution to their criminal activity. When attempting to acquire a license, the fictitious company DocSoft, allegedly based in Kyiv, Ukraine, was detected by the Sophos security mechanisms. After the local partner suggested a video conference together with Sophos to rule out any misunderstandings, the transaction was canceled by the Conti Group.
More at Sophos.com
About Sophos More than 100 million users in 150 countries trust Sophos. We offer the best protection against complex IT threats and data loss. Our comprehensive security solutions are easy to deploy, use and manage. They offer the lowest total cost of ownership in the industry. Sophos offers award-winning encryption solutions, security solutions for endpoints, networks, mobile devices, email and the web. In addition, there is support from SophosLabs, our worldwide network of our own analysis centers. The Sophos headquarters are in Boston, USA and Oxford, UK.