
The 13th edition of the State of Software Security Report, publishes the trends in the software landscape and how security practices are evolving. Some of the results are worrying: 82 percent of applications developed in the public sector had at least one security vulnerability discovered, compared to 74 percent in private companies.
The State of Software Security study found that public sector applications tend to have more security vulnerabilities than private sector applications. The higher number of errors and vulnerabilities in applications correlates with an increased security risk. The study was conducted against the background of a number of global government initiatives to improve cybersecurity, such as the EU Cyber Resilience Act, which aims to introduce additional minimum security requirements for products with digital elements. Analysis of data from more than 27 million scans in 750.000 applications formed the basis of Veracode's latest annual report
Many applications with security holes
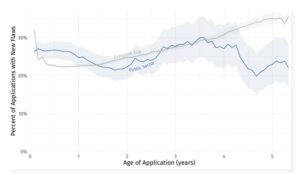
🔎 The public sector has had fewer vulnerabilities over the years than other organizations (Image: Veracode).
The researchers found that around 82 percent of the applications developed by public sector organizations had at least one security vulnerability. This compares to 74 percent for private companies. The data for the study were collected within the last 12 months. Depending on the type of vulnerability identified, there was a 12-7 percent higher likelihood that a vulnerability had been built into public sector applications in the last 12 months.
The numbers alone do not reflect the consequences that occur when hackers exploit bugs and vulnerabilities. In August last year, for example, a supply chain attack on the German Chamber of Commerce and Industry meant that they had to completely shut down their IT systems and digital services, telephones and e-mail servers. Essential services were available again shortly after the attack, but it took more than a month before full functionality was restored.
Serious vulnerabilities in the public sector
When it comes to “high severity” vulnerabilities, public sectors have the upper hand. Over the 12-month period of the study, the percentage of applications with critical security vulnerabilities was lower in the public sector (16,5%) than in private companies (19%). Higher severity vulnerabilities have a higher potential to affect the entire system if exploited.
Modern application testing encourages the use of security scanning tools such as Static Application Security Testing (SAST) and Software Composition Analysis (SCA). Different types of scans can uncover different types of vulnerabilities. SAST and SCA found a lower percentage of defects in public sector applications than in private enterprise applications.
Better safe than sorry
There is a big difference between the public and private sectors when it comes to the rate at which scans find new vulnerabilities in aging software. For applications that have been in use for 5 years, security deficiencies are increasing in the private sector, while they are decreasing in public organizations. This trend shows that public sector organizations pay attention to the security of their applications over several years and not only at the very beginning of the life cycle.
The 'State of Software Security Public Sector 2023 Report' recommends four actions that government agencies can take to improve their cybersecurity posture:
- Catch up: Backlogs of known bugs need to be fixed as soon as possible.
- Frequent scanning: Irregular scanning makes it harder to fix errors and leads to more backlogs.
- Automate: By automating tests via APIs, errors and defects in applications are better avoided.
- Adding DAST to the security stack: Use dynamic scanning to discover vulnerabilities that other scan types miss.
“The public sector has come a long way in improving the security of its applications. However, there is still much work to be done to enable authorities to improve their cyber security and ward off new threats. By focusing their security efforts on the root cause of most cyber breaches—the application layer—they can make significant improvements. Regular scans using various testing methods and subsequent vulnerability remediation will pave the way to a safer future for the public sector,” said Julian Totzek-Hallhuber, Manager Solution Architects EMEA & APAC at Veracode.
More at Veracode.com
About Veracode
Veracode stands for intelligent software security. The Veracode Software Security Platform finds flaws and vulnerabilities at every stage of the modern software development cycle. Thanks to powerful AI trained on trillions of lines of code, Veracode customers fix errors faster and with high accuracy.
