
Data protection, access management, cloud security, incident detection and handling and business continuity: CyberVadis study reveals potential gaps that lead to an increased third party risk.
CyberVadis, a leading company for third party cybersecurity risk assessments, has published a new study to analyze the cybersecurity measures declared by companies compared to the evidence-based assessments from CyberVadis. The report focuses on five key areas of cybersecurity - data protection, access management, cloud security, incident detection and handling, and business continuity - to uncover potential loopholes that could lead to increased third party risk through uncertified assessments.
Third party cybersecurity risk assessment
CyberVadis combines the speed of automation with the accuracy of a team of experts and involves vendors directly in cybersecurity assessments. CyberVadis validates the results with a team of security analysts and creates cybersecurity assessments that can be shared with other companies, along with a detailed improvement plan to strengthen your IT security.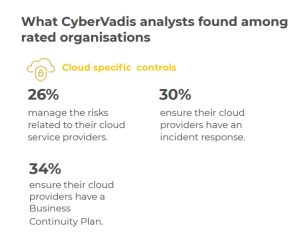
As more and more companies use third-party services, the risk of sensitive data increases. However, many do not properly understand the security situation of their supply chains or do not monitor them adequately. The main reasons for this shortage are reduced resources or a lack of time. For this report, CyberVadis collected self-declared cybersecurity controls from more than 1.200 organizations and compared the results with its own assessments based on a thorough, certified demonstration of these measures.
The main findings of the report include
Data protection due diligence doesn't always extend to procurement
While most organizations are aware of GDPR requirements, too many focus on internal data processing policies and overlook the threat posed by third parties. CyberVadis analysts found that less than one in three companies (29%) assessed the risks associated with possible non-compliance with data protection regulations. While 49% of companies train their employees in appropriate data protection practices, only 22% ensure that their procurement process includes dedicated controls for compliance and data protection.
Organizations allow remote access, but not always securely
As the COVID-19 pandemic accelerated the move to remote operations, two-thirds (62%) of companies said they allow remote access to their systems. CyberVadis found that only 44% of them provided a secure remote access solution. Somewhat more worrying is that only 37% have implemented advanced authentication methods for accounts with high privileges and only 25% of the companies evaluated have defined third-party access management.
There is room for improvement in the procurement and management of cloud providers
As another demonstration of rapid migration to the cloud, 81% of companies said they are currently using cloud models. However, there is a serious risk of malicious security breaches from misconfigured clouds, and the report found that this is the area where most improvement is needed. CyberVadis assessments showed that only 26% of organizations manage the risks associated with their cloud providers, 30% ensure that their cloud providers have an incident response strategy, and 34% ensure that their cloud providers have a Business continuity plan in place.
Incident management processes do not include SIEMs or prevent recurrence
For today's businesses, data breaches are a “when?” Rather than “if?” Question, so they need to take appropriate preparation. Of central importance here are strong capabilities for detecting and responding to incidents, which make it possible to contain cyber attacks at an early stage before permanent damage occurs. Fortunately, 75% of the companies evaluated have defined an incident management process, but only 32% have implemented a Security Information and Event Management (SIEM) solution and only 32% have a "Lessons Learned" process to identify the cause of incidents identify and reduce the likelihood of recurrence.
Crisis management is missing across the board, but organizations are committed to it
2020 has shown how important it is to prevent unplanned events and take the necessary measures to deal with a critical situation. Nevertheless, the report shows various shortcomings in crisis management in the organizations assessed. In their first self-assessment, 95% of company managers name this as a potential for improvement. CyberVadis reviews confirm this as only 44% of the companies evaluated have defined a business continuity plan and 22% test their plan on a regular basis. The CyberVadis analysts also found that only 24% of the companies assessed have defined crisis management and only 4% carry out regular crisis exercises. This is worrying because a good crisis management plan requires the dedicated team to be well trained and prepared to respond promptly in the event of a major event.
Methodology of the report
CyberVadis collected data on the cybersecurity controls declared by 1.289 organizations in the USA, EMEA and APAC and assessed them with standardized, analyst-validated audits via the CyberVadis platform. The full report can be read online and also downloaded.
More at CyberVadis.com
About CyberVadis
CyberVadis offers companies a cost-effective and scalable solution for third-party cybersecurity risk assessments. For a fixed annual fee, we carry out an unlimited number of evidence-based assessments via the CyberVadis platform. Our intuitive and user-friendly platform is based on a methodology that conforms to all major international compliance standards, including NIST, ISO 27001, GDPR and many other data protection and security laws. The CyberVadis solution combines the speed of automation with the accuracy and effectiveness of our team of experts.
