The number of compliance violations and security vulnerabilities in open source software is increasing: Audit teams discover a total of 230.000 critical cases. Revenera Status Report 2022 on Software Supply Chain & Open Source Software (OSS).
Revenera, provider of solutions for software monetization, open source compliance and installation, has published the new "State of the Software Supply Chain Report". Data from over 100 audits was analyzed to understand the volume of undocumented open source software (OSS) in companies and to identify potential compliance and security risks.
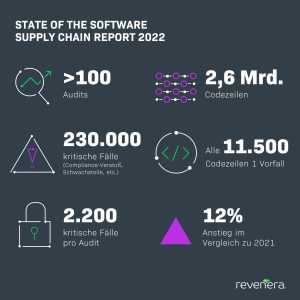
Up to 2.200 critical cases per audit
For the cross-industry study, Revenera evaluated more than 2,6 billion lines of code. The audit teams discovered a total of 230.000 critical cases. On average, every 11.500 lines of code, analysts encountered a compliance violation, security vulnerability, or something similar. On average, 2.200 critical cases come to light per audit. Compared to the previous year (2021: 1.959), the number of potential risks increased by 12%.
83% of the risks revealed in the audits were not known to the companies prior to the investigation. A common reason for operational blindness when it comes to OSS is the lack of software composition analysis (SCA) tools that scan applications at the code level and automatically report compliance violations and security vulnerabilities.
The most important results at a glance
The number of incidents classified as critical compliance risks (priority level 1) grew by 9.500% to 6 (2021: 9.000).
Revenera's audit team saw a significant jump in Severity 2 (e.g., secondary issues with commercial licenses) and Severity 3 (e.g., issues related to permissive BSD, Apache, or MIT licenses) incidents. Here it took off the number increased by 50% and 34% respectively. The increase indicates an increasing spread of OSS in applications and thus a growing risk for a wide range of industries.
The number of code-level vulnerabilities has more than tripled compared to the previous year.
Revenera analysts identified an average of 282 vulnerabilities per audit, an increase of 217% (2021: 89). Of the vulnerabilities discovered, 27% represented a "high" CVSS risk (Common Vulnerability Scoring System) and thus an immediate threat to IT security and cyber protection.
The proportion of binaries in a typical application code base continued to increase by 7%.
Overall, the analysts came across a total of 343.000 binaries that come from different collections of compiled source code. This also increases the complexity of the software code, since more dependencies are automatically included in the code base.
Since 2021: USA with new cybersecurity requirements
In view of the growing complexity of software code, Revenera expects SCA solutions and processes to spread more widely in companies over the next few years - especially as the regulatory framework conditions along the software supply chain are becoming increasingly strict.
It was not until 2021 that the USA laid down new cybersecurity requirements with an Executive Order (EO). Accordingly, software vendors must provide a Software Bill of Materials (SBOM) and implement automated tools and processes to verify code integrity. The EU Commission is going in a similar direction with its Open Source Software Strategy 2020-2023. Standard formats such as SPDX (Software Package Data Exchange), CycloneDX and SWID (SoftWare IDentification) are intended to help pass on information along the supply chain and standardize the creation of the SBOM.
More at Revenera.com
About Revenera
Revenera supports product managers to develop better applications, reduce time to market and effectively monetize products - whether on-premise, embedded software, SaaS or cloud. Revenera's leading solutions enable software and technology companies to grow their revenue with advanced software monetization. Software usage analyzes allow deep insight into the use of software and compliance with licensing. Software composition analysis solutions guarantee a high level of open source security and license compliance.