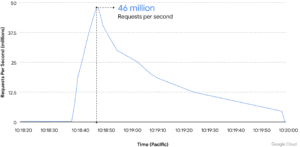
Google also offers the Cloud Armor service in its cloud services. This is intended to protect customers from DDoS attacks. In June, the network repelled the largest ever DDoS attack (layer 7) with 46 million requests per second.
In recent years, Google has observed that distributed denial of service (DDoS) attacks are increasing exponentially in frequency and size. Today's internet-facing workloads are at constant risk of attack. The impact degrades the performance of legitimate users. In addition, there are increased operating and hosting costs up to the complete unavailability of business-critical workloads.
46 million hits PER second!
On June 1st, a Google Cloud Armor customer became the target of a series of HTTPS DDoS attacks, peaking at 46 million requests per second. This is the largest Layer 7 DDoS reported to date - at least 76% larger than the previously reported record. To give a sense of the scale of the attack, this is roughly equivalent to getting all daily queries to Wikipedia in just 10 seconds.
Cloud Armor Adaptive Protection was able to detect and analyze traffic early in the attack lifecycle. Cloud Armor alerted the customer with a recommended protection rule, which was then deployed before the attack reached its full extent. Cloud Armor blocked the attack and ensured the customer's service stayed online and continued to serve its end users.
Botnet with devices from 132 countries
In addition to the unexpectedly high volume of traffic, the attack had other notable features. There were 5.256 source IPs from 132 countries contributing to the attack. These 4 countries, Indonesia, Brazil, India and Russia alone contributed approximately 31% of the total attack traffic. The attack used encrypted requests (HTTPS), which would have required additional computing resources to generate. Although stopping the encryption was necessary to inspect the traffic and effectively mitigate the attack, Google's use of HTTP pipelining required relatively few TLS handshakes.
Approximately 22% (1.169) of source IPs corresponded to Tor exit nodes, even though request volume from these nodes represented only 3% of attack traffic. Although we believe Tor's involvement in the attack was random due to the nature of the vulnerable services, our analysis shows that even at 3% of the peak (more than 1,3 million U/s), Tor exit nodes experienced a significant Web applications and services can send a lot of unwanted traffic to Tor.
More at Google.com