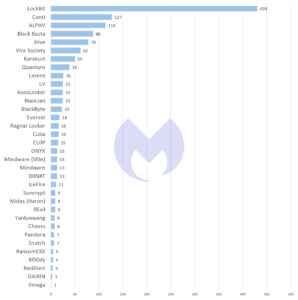
As in the previous months, LockBit remained by far the most active ransomware in August. Only then does triple extortion follow: the attack with DDoS in addition to encryption and blackmail. At least that is what the current August ransomware report by Malwarebytes shows.
Malwarebytes' threat intelligence team attributed 2022 attacks to the ransomware group in August 62 (compared to 61 attacks in July 2022 and 44 attacks in June 2022). For REvil, however, Malwarebytes only noted one attack in August. RansomEXX reports its first victim in four months and Snatch is also back with an attack after 40 days of inactivity. Interestingly, the victim listed on the Snatch website was also listed on REvil in April. However, it is not uncommon for victims to be attacked multiple times. This conspicuousness does not necessarily indicate a cooperation.
Conti, REvil, DarkSide duck their heads
As already described in the June ransomware report, part of LockBit's success is due to the fact that the ransomware group has so far avoided fatal missteps such as Conti, REvil or DarkSide. However, based on their activity, it can be assumed that this group has already attracted the attention of US law enforcement agencies. Between March 2022 and August 2022, LockBit carried out 430 known attacks in 61 different countries. LockBit was responsible for every third known ransomware attack during this period. Between March 2022 and August 2022, Malwarebytes attributed the group an average of around 70 attacks per month, while the average for the other groups monitored by Malwarebytes never exceeded seven.
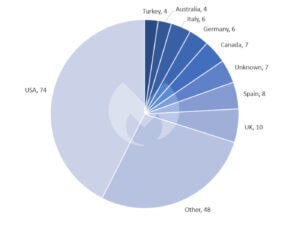
When it comes to the distribution of ransomware attacks by country, the USA was again by far the most frequently affected by ransomware attacks in August 2022 with 74 attacks. However, according to Malwarebytes, this is more due to the size of their service sector and thus the large number of potential victims than to a specific targeting. Ten attacks took place in the UK, eight in Spain, seven in Canada and six in Germany.
The Future of Ransomware: New Tactics
In August, two events indicated how ransomware groups' tactics could evolve beyond "double extortion" - the biggest innovation in ransomware tactics in recent years. Originally, encrypted ransomware files and the groups behind them demanded a ransom in return for a decryption tool. It was almost impossible to decrypt the files without this tool. The victims could only avoid paying the ransom by restoring the encrypted files from backups.
Finally, in late 2019, the group behind the Maze ransomware began stealing files from their victims before encrypting them. She threatened to post the stolen files on the dark web. This gave victims an incentive to pay the ransom even if they were able to restore their system from backups. This tactic was quickly copied and is now the standard for large ransomware groups.
Triple attack: DDoS, encryption, extortion
The strategy of triple blackmail is new: In August, LockBit stole data from the cyber security company Entrust in a double-extortion attack. According to LockBit, the victim's unusual response was to prevent the ransomware group from releasing the stolen data by launching a distributed denial-of-service (DDoS) attack against the group's leak site. This attack delayed the data leak but does not appear to have prevented it. However, he inspired LockBit to now try the same thing. After seeing how effective DDoS attacks can be, the group announced on a hacker forum that they now plan to use DDoS as a third baton against their victims, alongside encryption and extortion. In the text, LockBit referred to the tactic as "triple extortion".
The statements of ransomware groups must always be taken with a pinch of salt. However, potentially endangered companies should take the warning seriously, because the procedure is actually not new. DDoS extortion is an older tactic than encrypting files and demanding a ransom. It's just been used less in recent years.
Will ransomware eventually go away?
Data leakage is such a successful tactic that some groups, such as Karakurt, no longer bother encrypting files. They totally rely on the threat of the stolen and leaked data. Malwarebytes' threat intelligence team believes more gangs will take this approach in the future.
Since ransomware groups began using "big game" tactics about five years ago, the skills required for a successful attack have changed. In a "big game" attack, the encrypting malware is only one resource. The success of an attack, on the other hand, lies in the ability to find a target, understand its value, and then break into its network without being detected.
This has led to significant specialization, with some criminal groups providing the software, others acting as access brokers, and still others ultimately actually performing the attacks. The capabilities that access brokers and attackers have developed can be used not only for spreading ransomware, but also for surveillance, sabotage, espionage, and data exfiltration.
Sanctions also make it harder for ransomware groups
So if ransomware no longer generates any significant revenue, it must be assumed that cybercriminals will simply use other forms of attack. The pressure to do so began with improved backups - and has been compounded by Russia's war in Ukraine. Since the beginning of the war, it has become even more difficult for ransomware groups to receive ransom payments due to the threat of sanctions. Some experts in the security industry are therefore predicting the imminent end of ransomware.
Malwarebytes, on the other hand, doesn't expect a sudden change, although the long-term trend is certainly one of groups moving away from encryption. In fact, some groups are finding it increasingly difficult to enforce their claims without encryption. In addition, encryption remains the tactic of choice for one of today's most successful ransomware groups: LockBit.
New ransomware groups in August
It also seems that the cybercriminals themselves have not yet realized the imminent end of ransomware-as-a-service. As in July, some new groups appeared in August: D0nut with 13 attacks, IceFire with 11 attacks, Bl00dy with 5 attacks and DAIXIN with 3 attacks. Bl00dy is striking: The group does not have a leak site, but instead uses the messaging app Telegram.
More at Malwarebytes.com
Via Malwarebytes Malwarebytes protects home users and businesses from dangerous threats, ransomware and exploits that are undetected by antivirus programs. Malwarebytes completely replaces other antivirus solutions in order to avert modern cybersecurity threats for private users and companies. More than 60.000 companies and millions of users trust Malwarebyte's innovative machine learning solutions and its security researchers to avert emerging threats and eliminate malware that antiquated security solutions fail to detect. You can find more information at www.malwarebytes.com.