The July 2022 ransomware report from Malwarebytes shows little news. LockBit and Black Basta continue to lead in attack statistics. What is new, however, is the appearance of the ransomware REvil (also known as Sodinokibi), which was believed to be dead.
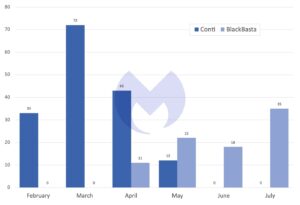
As in previous months, LockBit remains by far the most active ransomware. Malwarebytes' threat intelligence team attributed 2022 attacks to the ransomware group in July 61 (compared to 44 attacks in June 2022 and 73 attacks in May 2022). Black Basta, a relatively new ransomware variant that first emerged in April 2022, follows LockBit with 35 attacks over the past month. The ransomware group is closely associated with the Conti gang and comes closest to the group as a possible successor. Two other ransomware groups associated with Conti are Hive and Karakurt. Both were also very active in July 2022 - with 26 and 19 attacks respectively.
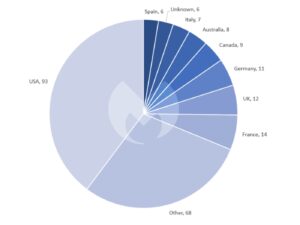
Ransomware: USA remains the most affected
When it comes to the distribution of ransomware attacks by country, in July 2022 the USA was repeatedly by far the most frequently hit by ransomware attacks. Malwarebytes associates 93 attacks with the United States. 14 attacks took place in France, 12 attacks in the UK and 11 attacks in Germany.
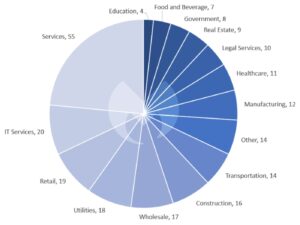
In July 2022, the service sector again took first place among the industries. The Malwarebytes Threat Intelligence team attributes almost a quarter of all detected international ransomware attacks to this industry. Services are followed by IT services with 20 attacks, trade with 19 attacks and utilities with 18 attacks.
LockBit: Connection to DarkSide/BlackMatter
In the June ransomware report, Malwarebytes reported extensively on LockBit and the launch of LockBit 3.0. The group's success appeared to be due in part to the fact that it was completely focused on its business while other gangs were busy with attention-grabbing activities. However, this interpretation may have been premature.
In July, in an interview with Red Hot Cyber, LockBit expressed its view that criminal hackers contribute to security: “We are ordinary pentesters and we make the world more secure, thanks to us companies can learn a security lesson and close vulnerabilities. However, the interview also contained some useful information - for example, that between 50 and XNUMX percent of LockBit victims pay the ransom. The attack numbers reported by Malwarebytes in its monthly ransomware reports relate solely to victims who turned up on leak sites because they didn't pay the ransom.
In the interview, LockBit also confirmed the suspected relationship between LockBit 3.0 (aka LockBit Black) and DarkSide/BlackMatter ransomware. The interviewee revealed that LockBit paid for the DarkSide source code and on the basis of which LockBit 3.0 was developed.
DarkSide is the ransomware used in the May 2021 Colonial Pipeline attack. The DarkSide group disappeared shortly after the attack, allegedly due to US pressure. She reappeared as BlackMatter in July 2021 before disappearing again in October 2021.
Black Basta: Connection to Conti
Black Basta first appeared in Malwarebytes' ransomware report in April 2022 with 11 attacks. In May, the group was second with 22 attacks, third in June with 18 attacks, and second again in July with 35 attacks. The fact that the ransomware group had so many victims as early as April led some to suspect that this must be the work of an established gang with a network of experienced partners. Since then, Black Basta has been associated with Conti.
This year, the Continental Group hatched a plan to fake its own death. The group's rapprochement with the Russian state probably led to ransom payments drying up. The members of the group were then allegedly distributed to other Conti "brands" or to other ransomware groups that Conti is associated with.
The obvious beneficiaries include three out of five of July's most prevalent ransomware variants: Black Basta, Hive, and KaraKurt.
REvil returns
Besides LockBit and Black Basta, July was also marked by the reappearance of REvil (aka Sodinokibi). For the first time since May, a victim appeared on the group's Tor Leak website in July. While many other groups were far more active, this ransomware group's reputation ensures that any sign of life must be taken seriously.
REvil is responsible for two of the most significant ransomware attacks in history, both occurring in 2021: the attack on JBS, the world's largest meat producer, and the attack on the Kaseya VSA supply chain. The attack on Kaseya ended when the company announced it had acquired the decryption key needed to free the victims without paying REvil's $70 million ransom. It later turned out that the FBI was the source of the key.
Since then, REvil has lived an erratic life. Under pressure from US law enforcement agencies, the group disappeared from the scene in July 2021. It resurfaced a few months later, before finally being taken offline in October when its infrastructure was hijacked by a multi-state law enforcement operation. In January 2022, the FSB arrested eight of its members. But even that wasn't enough to keep the gang grounded for long.
New ransomware groups are emerging
A number of new ransomware groups also emerged in July. New additions include BianLian, Yanluowang, RedAlert, Omega and Cheers. With 11 known victims, BianLian's debut is comparable in size to Black Basta's April 2022 release, so Malwarebytes will be keeping an eye on the group.
More at Malwarebytes.com
Via Malwarebytes Malwarebytes protects home users and businesses from dangerous threats, ransomware and exploits that are undetected by antivirus programs. Malwarebytes completely replaces other antivirus solutions in order to avert modern cybersecurity threats for private users and companies. More than 60.000 companies and millions of users trust Malwarebyte's innovative machine learning solutions and its security researchers to avert emerging threats and eliminate malware that antiquated security solutions fail to detect. You can find more information at www.malwarebytes.com.
Matching articles on the topic
[starbox id=USER_ID] <🔎> ff7f00