
New research from Trend Micro reveals how the ransomware industry is staying alive. A new study shows how cybercriminals operate and finance their activities. In it, the threat experts found that only ten percent of the companies affected by ransomware actually pay their extortionists. However, these payments subsidize numerous other attacks.
The study contains strategic, tactical, operational and technical information on threats. Data science methods were used to compile various information about threat actors. These data and metrics help to compare groups of ransomware, assess risk and model the behavior of threat actors.
A paying victim funds 9 more attacks
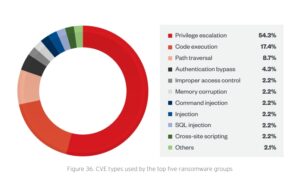
🔎 These vulnerability techniques - CVE types - were used by the APT groups to attack (Image: Trend Micro).
- The XNUMX percent of companies that pay a ransom tend to act quickly. As a result, they are often forced to accept higher demands for each further compromise.
- The risk level for attacks is not homogeneous. It varies by region, industry and company size.
In certain sectors and countries, those affected pay more often than in others. Therefore, companies in these industries and - Countries more likely to be targeted for attack.
- Paying a ransom often only increases the overall cost of an incident without bringing any benefits.
- January and the July-August period see the lowest activity of ransomware attackers. These are good times for defenders to rebuild their infrastructure and prepare for future threats.
The cybersecurity industry can help reduce the profitability of ransomware. To do this, stakeholders should prioritize protection in the early stages of the kill chain, thoroughly analyze ransomware ecosystems, and reduce the percentage of victims who pay. Findings from the Japanese cybersecurity provider's report may also help decision-makers better assess potential financial risks posed by ransomware.
Insights open up a number of possibilities
- IT leaders can justify higher budgets for ransomware mitigation.
- Governments can better plan their budgets for attack recovery support and law enforcement.
Insurers can calculate the prices for their services more precisely. - International companies can better compare ransomware to other global risks.
“Ransomware is a major threat to businesses and governments. It is constantly evolving, which is why we need more accurate data-driven risk modeling methods in this context,” explains Richard Werner, Business Consultant at Trend Micro. "Our new study is designed to help IT decision makers better understand their risk and give policy makers the information they need to develop more effective and impactful countermeasures against cybercrime."
More at TrendMicro.com
About Trend Micro As one of the world's leading providers of IT security, Trend Micro helps create a secure world for digital data exchange. With over 30 years of security expertise, global threat research, and constant innovation, Trend Micro offers protection for businesses, government agencies, and consumers. Thanks to our XGen™ security strategy, our solutions benefit from a cross-generational combination of defense techniques optimized for leading-edge environments. Networked threat information enables better and faster protection. Optimized for cloud workloads, endpoints, email, the IIoT and networks, our connected solutions provide centralized visibility across the entire enterprise for faster threat detection and response.
