
Ransomware attacks consist of an ecosystem of actors. There is advertising for and provision of services and partnerships on specialized dark web marketplaces and forums. Ransomware operator receives a share of the profit between 20 and 40 percent, the rest remains with the partner. . Business access starts as low as $ 50.
Ransomware attacks that encrypt data and extort ransom affect companies of all sizes and in all sectors. It can easily give the impression that the actors are acting arbitrarily. In fact, there is a complex ecosystem behind it with many different actors, each of which takes on individual roles. On the occasion of the Anti-Ransomware Day, Kaspersky provides a new report [1] about the complex ecosystem behind ransomware.
Ransomware ecosystem is looking for partners
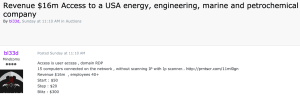
An example of an offer: Here the remote desktop access of a user to a company is offered (Image: Kaspersky).
Developers, bot masters, credential vendors, or ransomware operators: the ransomware ecosystem consists of a variety of players. They all offer different services via advertisements on the Darknet [2]. Independent, prominent professional groups don't typically visit such sites, but REvil, for example, which has increasingly targeted organizations in recent quarters, is now regularly posting its offers and news through affiliate programs. This creates a partnership between the ransomware operator and the customer, with the ransomware operator receiving a profit share of between 20 and 40 percent as the seller, while the remaining 60 to 80 percent remain with the "affiliate partner". Partner selection follows an elaborate process with rules set by ransomware operators – including geographic restrictions or political alignments, while ransomware victims are selected in a utility-maximizing manner.
Common pursuit of profit
Salesman and customer or partner are united by the common pursuit of profit, which is why the most infected organizations are often simpler goals to which access was particularly easy. Such accesses are auctioned on auction platforms or offered at fixed prices from 50 US dollars in darknet forums. The attackers are mostly botnet owners who participate in massive and widespread campaigns and sell access to their victims' devices in large quantities. On the other hand, sellers of access data are always on the lookout for publicly known vulnerabilities in software connected to the Internet, such as VPN applications or e-mail gateways, with which they can infiltrate organizations.
Ransomware operators typically sell malware samples and ransomware builders for $ 300 to $ 4.000. Another business model is Ransomware-as-a-Service, where ransomware is offered for $ 120 per month or $ 1.900 per year with ongoing support from its developers.
Clarify together about risks and take countermeasures
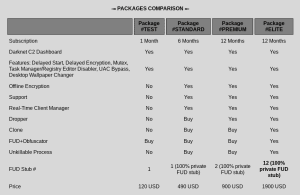
In the dark web, ransomware is offered as a subscription as various packages with a term of 1, 6 and 12 months with product information and prices (Image: Kaspersky).
"Over the past two years, we've seen cybercriminals become bolder when dealing with ransomware," said Craig Jones, Director of Cybercrime at INTERPOL. “Such attacks are no longer limited to large corporations and government organizations. Ransomware operators are ready to attack virtually any organization, regardless of its size. The ransomware industry is a complex one involving many different players with different roles. In order to do anything about it, we need to learn how it works and fight it as one. Anti-Ransomware Day is a good opportunity to raise awareness and remind the public of the importance of using effective security practices. INTERPOL's Global Cybercrime Program and our partners are fully committed to reducing the global impact of ransomware and protecting society from the harm caused by this growing threat."
Complex ransomware ecosystem
"The ransomware ecosystem is multifaceted and there are many interests at stake," adds Dmitry Galov, security researcher on Kaspersky's Global Research and Analysis Team (GReAT). “It's an ever-changing market with many players, some quite opportunistic, others very professional and savvy. They do not select specific targets, but may attack any organization, regardless of size, if they gain access to a system. Your business is thriving and will not go away anytime soon. Fortunately, fairly simple security measures can stop the attackers. Standard procedures such as regular software updates and backups already help.”
"Effective countermeasures against the ransomware ecosystem can only be taken once its fundamentals are truly understood," added Ivan Kwiatkowski, senior security researcher on Kaspersky's Global Research and Analysis Team (GReAT). "Through our report, we hope to help understand exactly how ransomware attacks are organized so that the IT security community can take appropriate countermeasures."
More SecureList at Kaspersky.com
About Kaspersky Kaspersky is an international cybersecurity company founded in 1997. Kaspersky's in-depth threat intelligence and security expertise serve as the basis for innovative security solutions and services to protect companies, critical infrastructures, governments and private users worldwide. The company's comprehensive security portfolio includes leading endpoint protection as well as a range of specialized security solutions and services to defend against complex and evolving cyber threats. Kaspersky technologies protect over 400 million users and 250.000 corporate customers. More information about Kaspersky can be found at www.kaspersky.com/
